Restrict Network Access with SentinelOne Singularity™
SentinelOne Singularity is an autonomous cybersecurity platform that provides comprehensive endpoint protection, detection, and response capabilities. The SentinelOne agent runs on your devices (endpoints), collecting and analyzing endpoint data to detect and respond to threats in real-time. The agent's presence on endpoints and the security data it collects can be utilized to enforce access policies and limit network access according to the "health" status of the endpoints.
The integration of NetBird with SentinelOne provides organizations with robust security controls that allow only IT-managed devices running SentinelOne to access the network. Additionally, the integration uses SentinelOne's threat detection capabilities, enabling administrators to further limit network access based on the security posture of each device.
SentinelOne's endpoint protection provides real-time threat detection and automated response capabilities. By integrating with SentinelOne Singularity, NetBird can ensure that only devices with active security monitoring and protection can access the network.
In this guide, we will walk you through the configuration steps to integrate SentinelOne Singularity with NetBird and use endpoint security status to control network access for devices that meet your security requirements.
Prerequisites
Before you start creating and configuring a SentinelOne integration, ensure that you have the following:
- A SentinelOne account with the permissions to create and manage API tokens. If you don't have the required permissions, ask your SentinelOne administrator to grant them to you.
Create a SentinelOne API Token
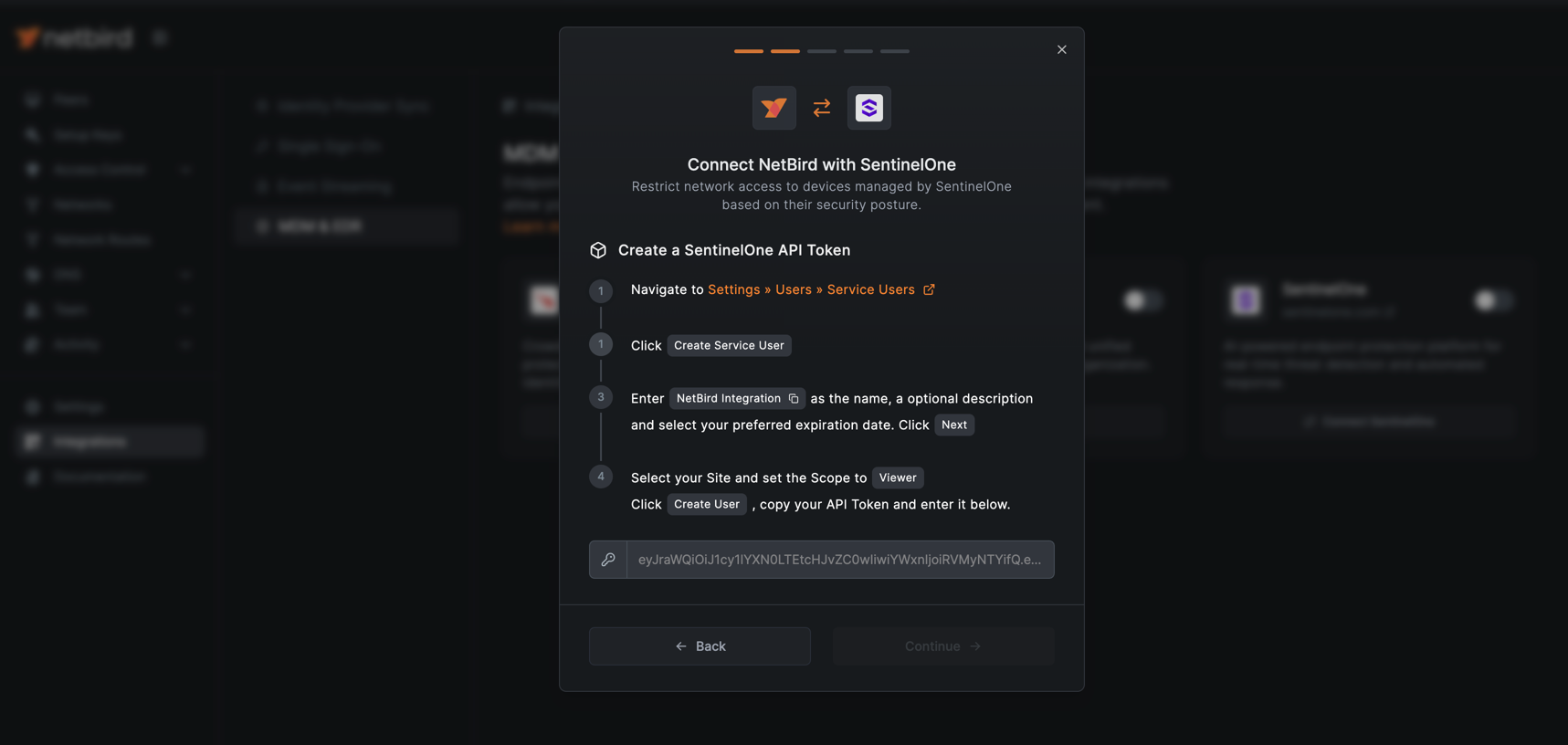
- Navigate to your SentinelOne Management Console
- Go to Settings » Users » Service Users
- Click Create Service User
- Fill in the form:
- Name:
NetBird Integration - Description:
API token for NetBird EDR integration(optional) - Expiration Date: Set your preferred expiration date
- Name:
- Click Next
- Select Site and set Scope to Viewer
- Click Create User
- Copy the generated API token immediately (it will only be displayed once)
- Note your SentinelOne console URL from your browser's address bar (e.g.,
https://your-tenant.sentinelone.net)
Treat the API token securely and store it safely. You will need both the console URL and API token for the NetBird integration configuration.
Configure a SentinelOne Integration in NetBird
- Navigate to the Integrations » EDR tab in the NetBird dashboard
- Click Connect SentinelOne to start the configuration wizard
- Click the Get Started button to initiate the integration process
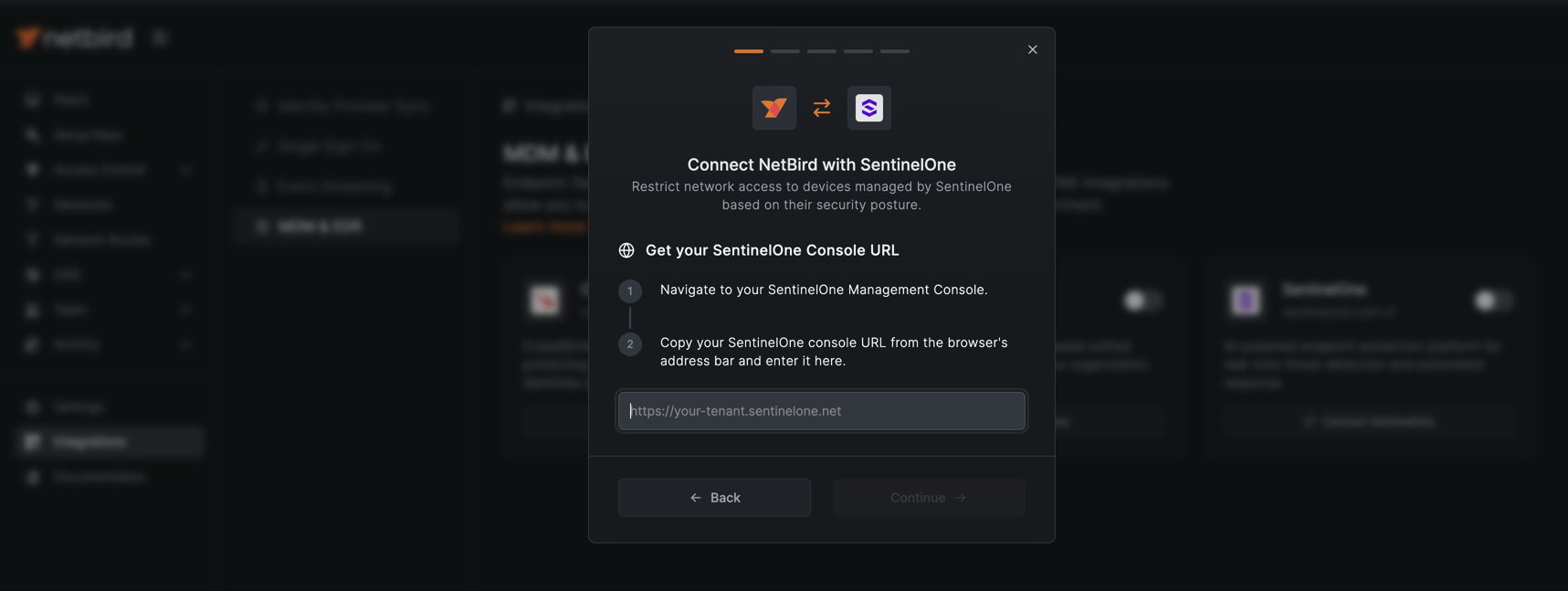
- Enter your SentinelOne console URL (e.g.,
https://your-tenant.sentinelone.net) and click Continue
- Enter the API token you created in the previous step and click Continue to verify the connection
- Select the groups you want to apply the integration to and click Connect
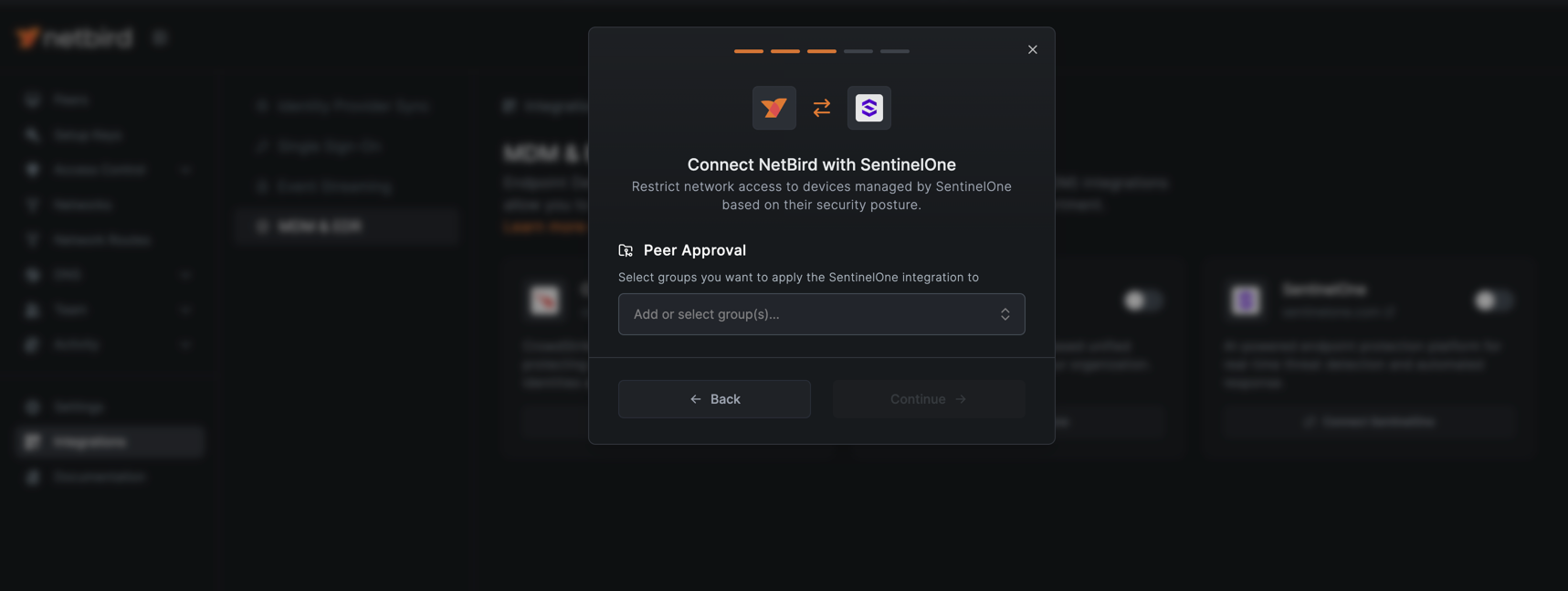
The EDR check will apply only to peers in the selected groups and will require a running SentinelOne agent. You can also use groups synchronized from your Identity Provider (IdP).
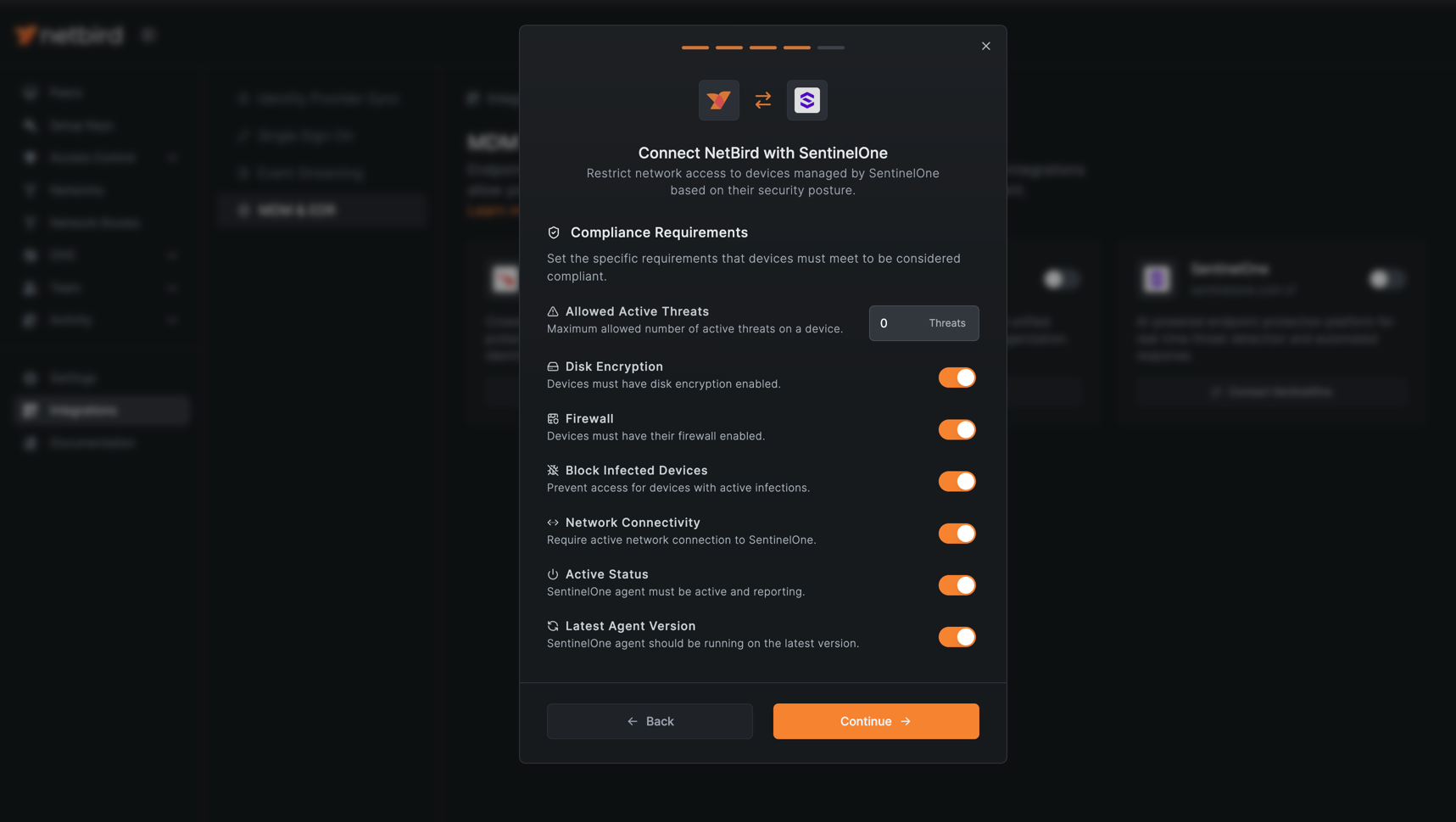
- Configure the compliance criteria that devices must meet to access your network. These security requirements ensure only healthy, properly configured devices can connect. Select the criteria that align with your organization's security policies:
- Allowed Active Threats: Maximum number of active threats allowed on a device. Default is set to
0to block devices with any active threats. - Disk Encryption: Requires disk encryption to be enabled on the device.
- Firewall: Requires the device firewall to be enabled and active.
- Block Infected Devices: Prevents network access for devices with confirmed active infections.
- Network Connectivity: Requires active network connection between the device and SentinelOne services.
- Active Status: Requires the SentinelOne agent to be active and reporting. The agent must be in operational state (not disabled, corrupted, or experiencing errors).
- Latest Agent Version: Requires the SentinelOne agent to be running the most current version.
- Allowed Active Threats: Maximum number of active threats allowed on a device. Default is set to
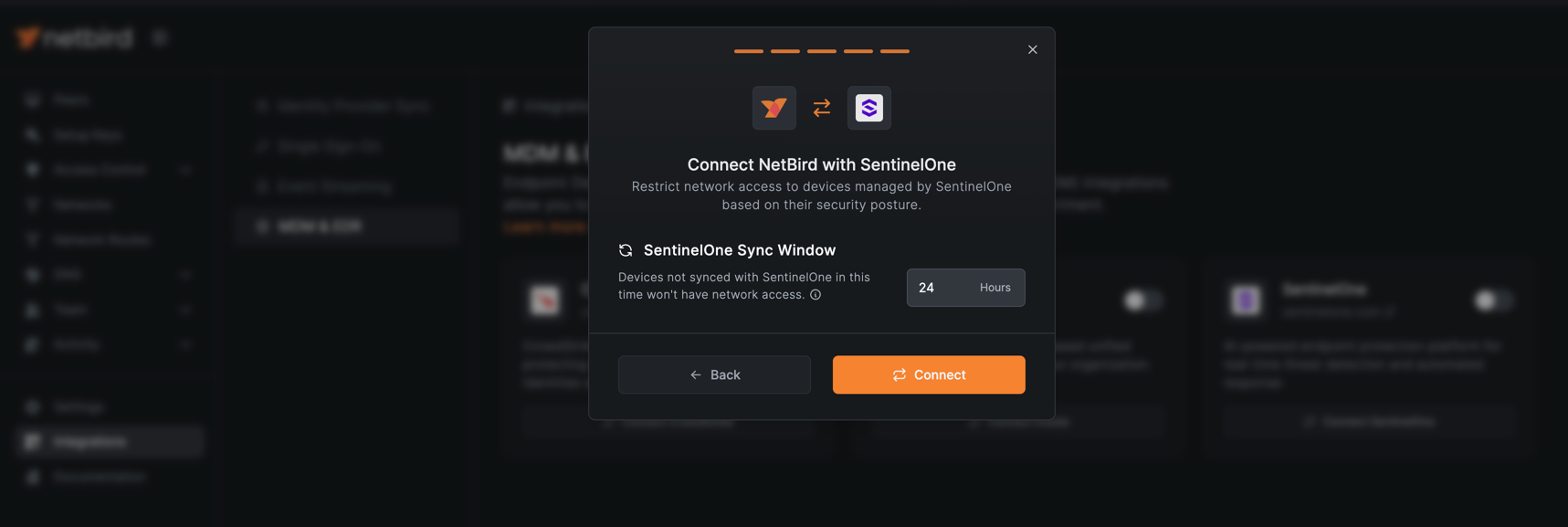
- Configure the SentinelOne Sync Window (default is 24 hours). This setting determines which devices NetBird will consider for network access based on their recent activity in SentinelOne. Only devices that have been active and reporting to SentinelOne within this time window will be synchronized. These devices must then also meet the configured compliance criteria to gain network access.
-
Click Connect to complete the integration setup
-
Only peers that have the SentinelOne agent installed and meet all the configured compliance criteria will be granted access to the network. Peers without the SentinelOne agent or those that don't meet the compliance requirements will appear with an
Approval requiredmark in the peers list and won't be able to access the network until they have the agent installed and satisfy all the specified security requirements.
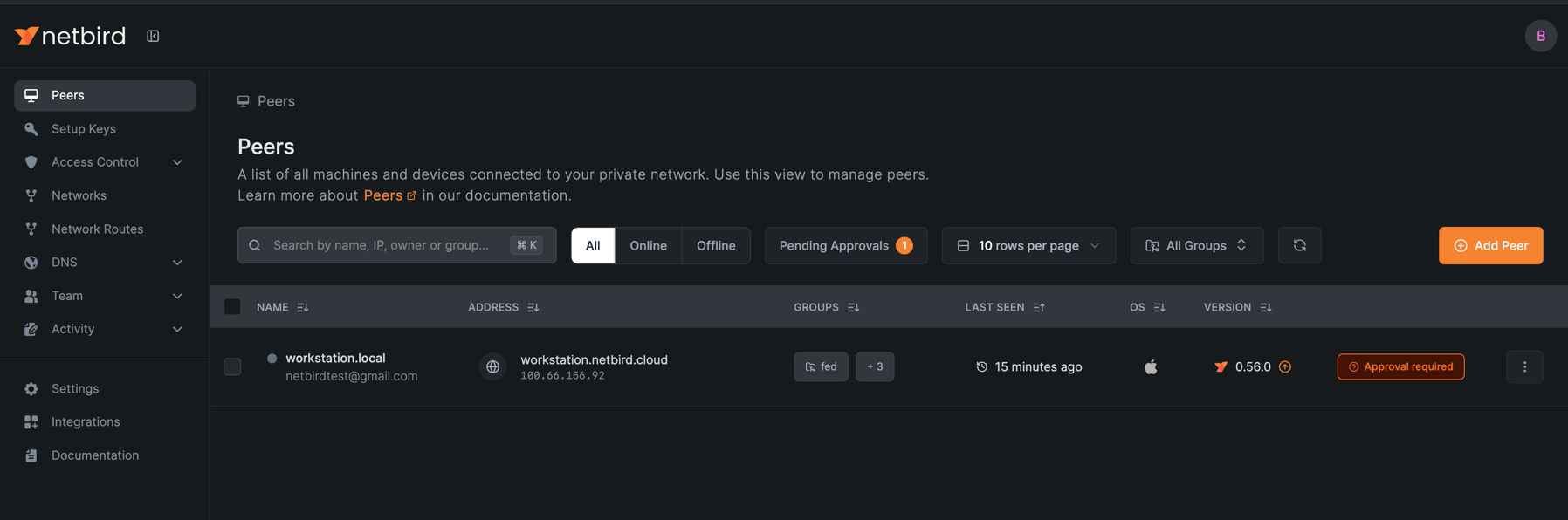
NetBird matches the SentinelOne agent to the peer using the Serial Number of the device. You must ensure that each of your devices has a unique serial number.

