Accessing entire domains within networks
This guide shows how to provide access to entire internal domains using NetBird Networks with wildcard domain resources. Wildcard domains simplify access management when teams need to reach multiple subdomains under a common parent domain.
Example scenario
An AI software company needs to provide secure access to two internal environments:
- Development environment (
*.dev.example.com): Shared workspace for code development, testing, and collaboration - AI model training environment (
*.ai.example.com): Sensitive AI models and datasets with restricted access
Using wildcard domains, developers can access any subdomain under *.dev.example.com, while data scientists access *.ai.example.com. This separation ensures team members only reach resources relevant to their roles.
Prerequisites
Before starting, ensure you have:
- NetBird clients installed on developer and data scientist devices
- Routing peers configured in your network using setup keys
- Nameservers configured in NetBird to resolve domain queries
Enable DNS wildcard routing
DNS wildcard routing allows NetBird to resolve subdomain requests through routing peers. This must be enabled before using wildcard domain resources.
DNS wildcard routing shifts DNS resolution from the local client to the routing peer, enabling access control rules and optimized traffic routing.
To enable DNS wildcard routing:
- Navigate to
Settings>Networksin NetBird - Toggle
Enable DNS wildcard routing
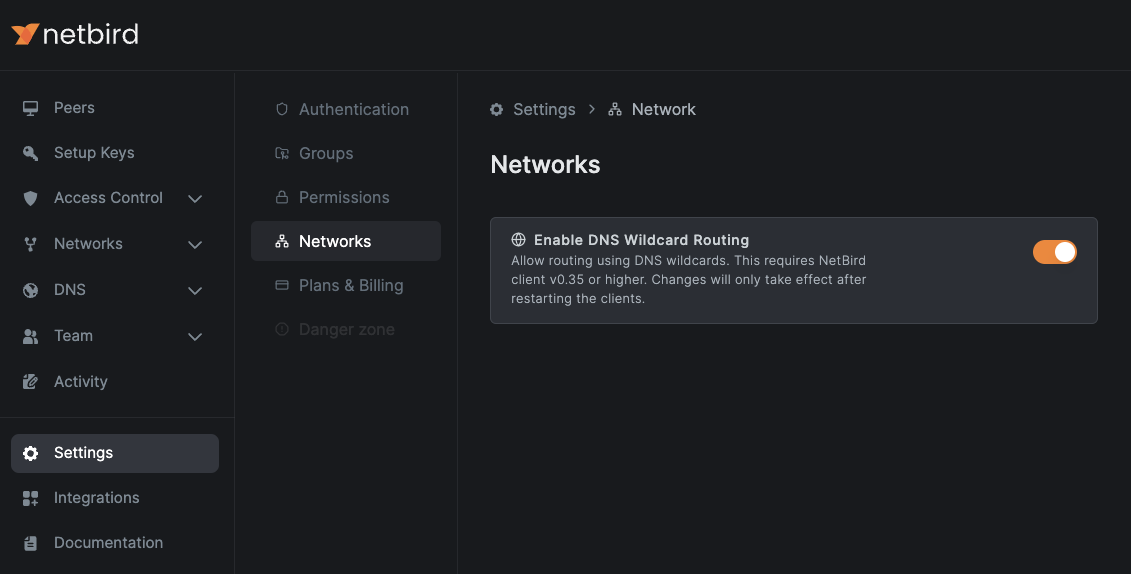
DNS wildcard routing requires routing peers and clients running version 0.35.0 or later. Restart your routing peers and clients after enabling this feature.
DNS Forwarder port change: Starting with NetBird v0.59.0, the local DNS forwarder switches from port 5353 to 22054 to avoid collisions. For backward compatibility, the Management Service applies the new port only when all peers in the account run v0.59.0 or newer.
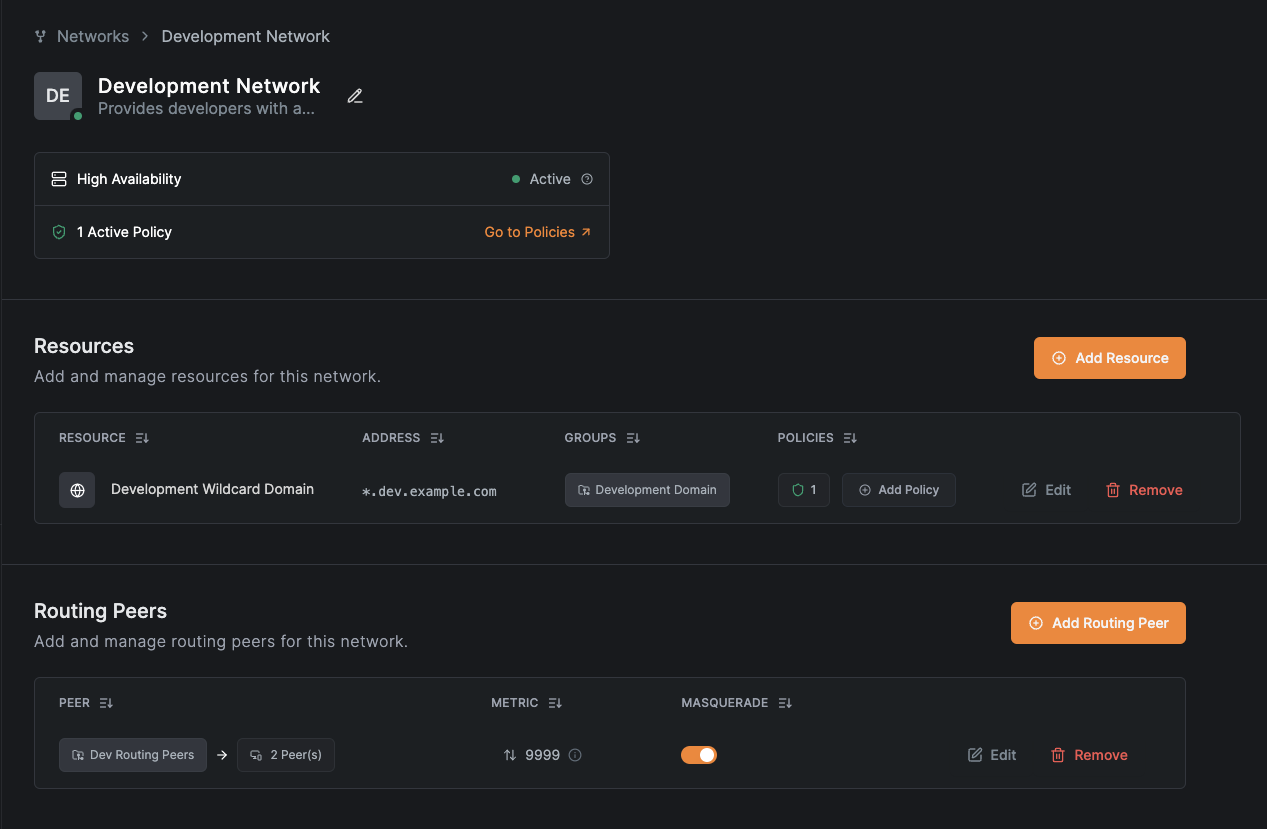
Set up the development network
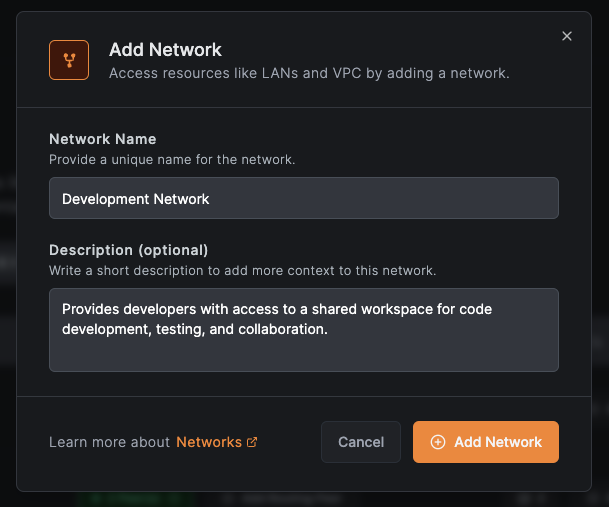
Create the network
- Navigate to
Networks>Networksin the NetBird dashboard - Click
Add Network - Enter a name (e.g.,
Development Network) and optional description - Click
Add Network
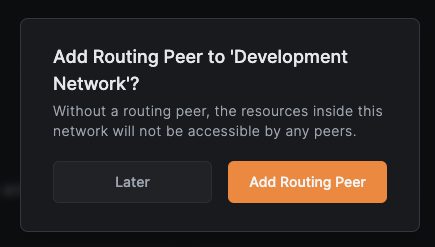
Add routing peers
Click Add Routing Peer to enable access to resources in this network.
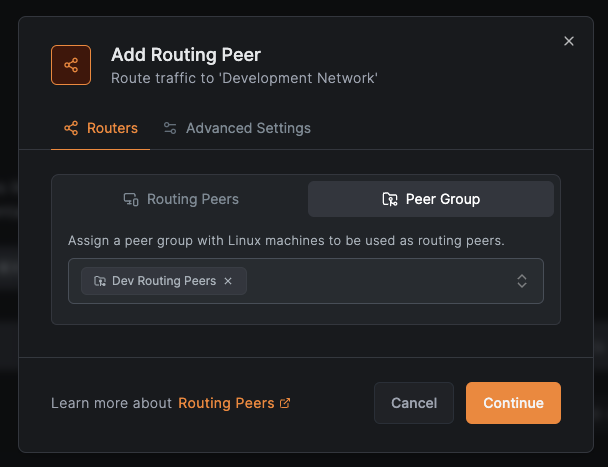
Choose your routing configuration:
- Select
Routing Peersto add a single peer - Select
Peer Groupto add multiple peers for high availability - Click
Continue
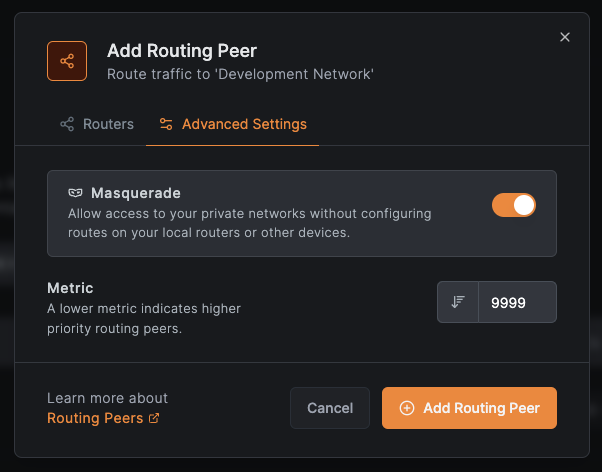
In Advanced Settings:
- Enable
Masqueradeto access private networks without configuring local routers - Set
Metricto prioritize routers (lower values = higher priority) - Click
Add Routing Peer
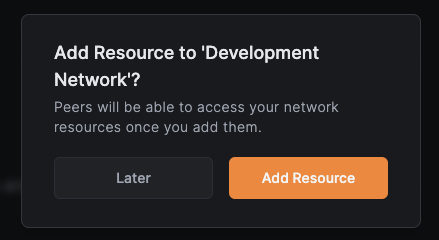
Add a wildcard domain resource
Click Add Resource to create the wildcard domain resource.
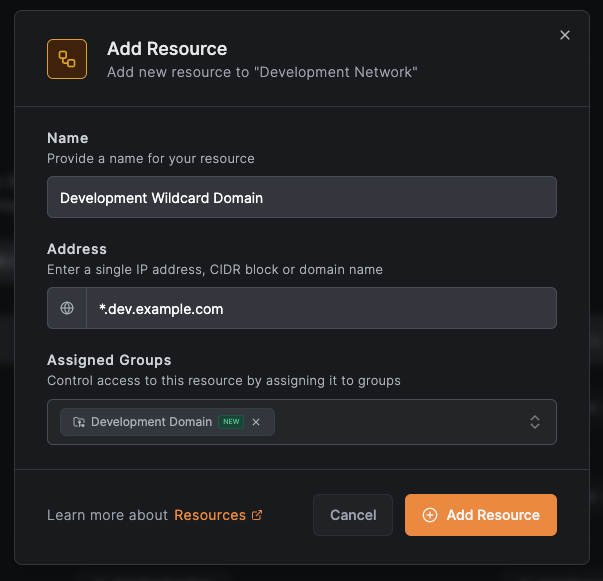
Configure the resource:
- Name:
Development Wildcard Domain - Address:
*.dev.example.com - Assigned Groups: Select or create a group (e.g.,
Development Domain) - Click
Add Resource
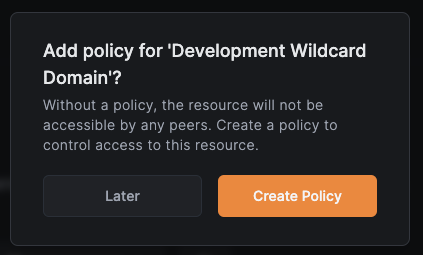
Create an access policy
Click Create Policy to grant developers access to *.dev.example.com.
Configure the policy:
- Protocol:
ALL - Source:
Developers - Destination:
Development Domain(auto-populated)
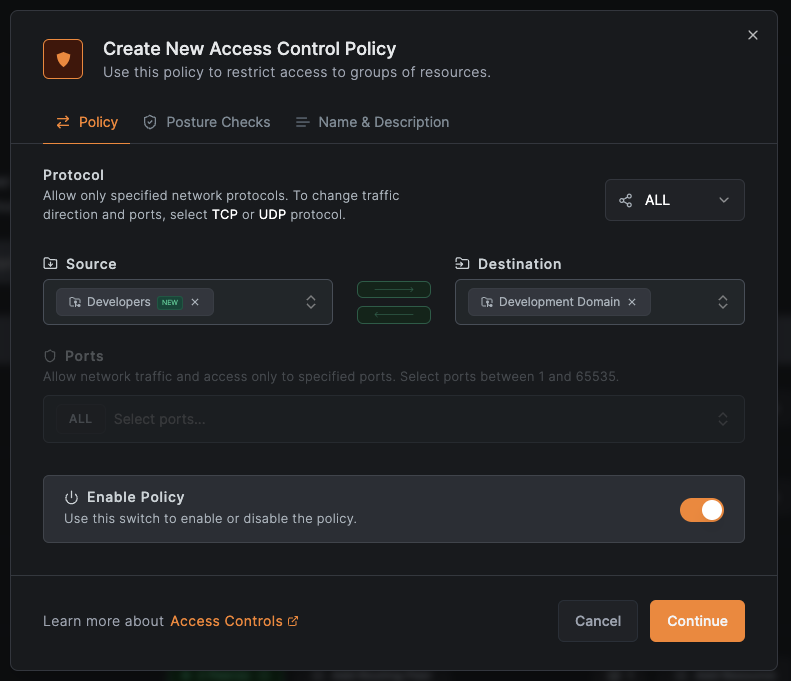
Click Continue to optionally add posture checks, then Continue again. Enter a policy name (e.g., Development Wildcard Domain Policy) and click Add Policy.
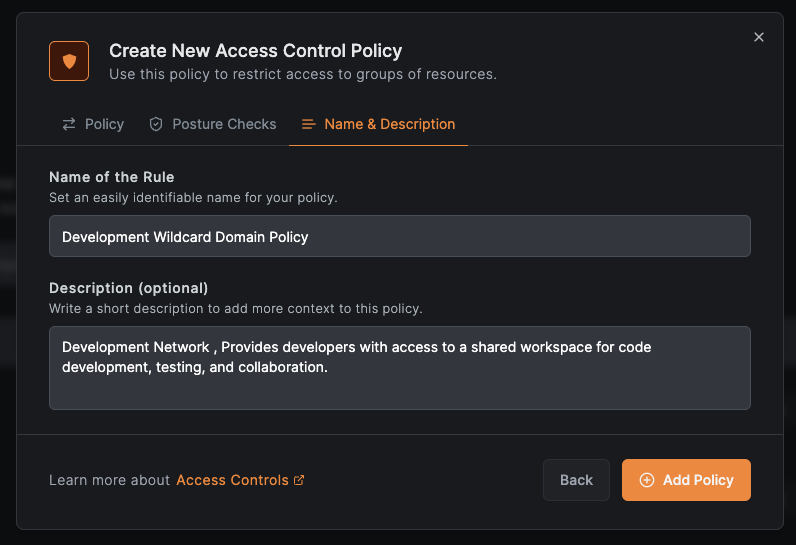
Add the base domain resource
Wildcard domains (*.dev.example.com) only match subdomains, not the base domain itself. To also allow access to dev.example.com, add it as a separate resource.
- Navigate to
Networks>Development Networkand clickAdd Resource
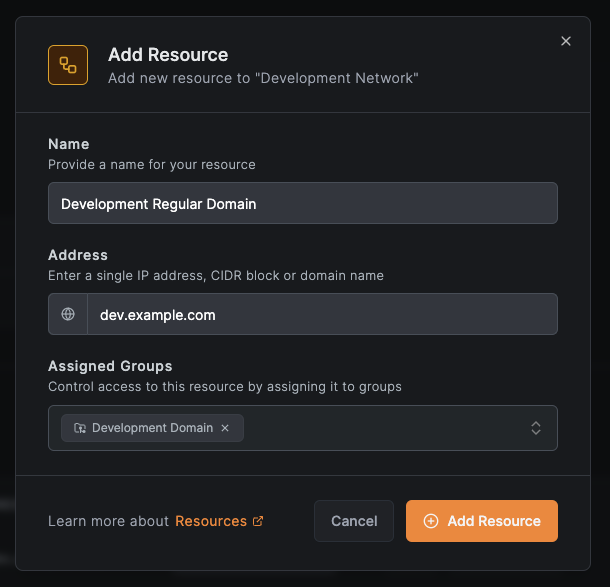
- Configure the resource:
- Name:
Development Regular Domain - Address:
dev.example.com - Assigned Groups:
Development Domain(same group as the wildcard) - Click
Add Resource
- Name:
Since you used the same group, NetBird automatically applies the existing routing peers and access policies.
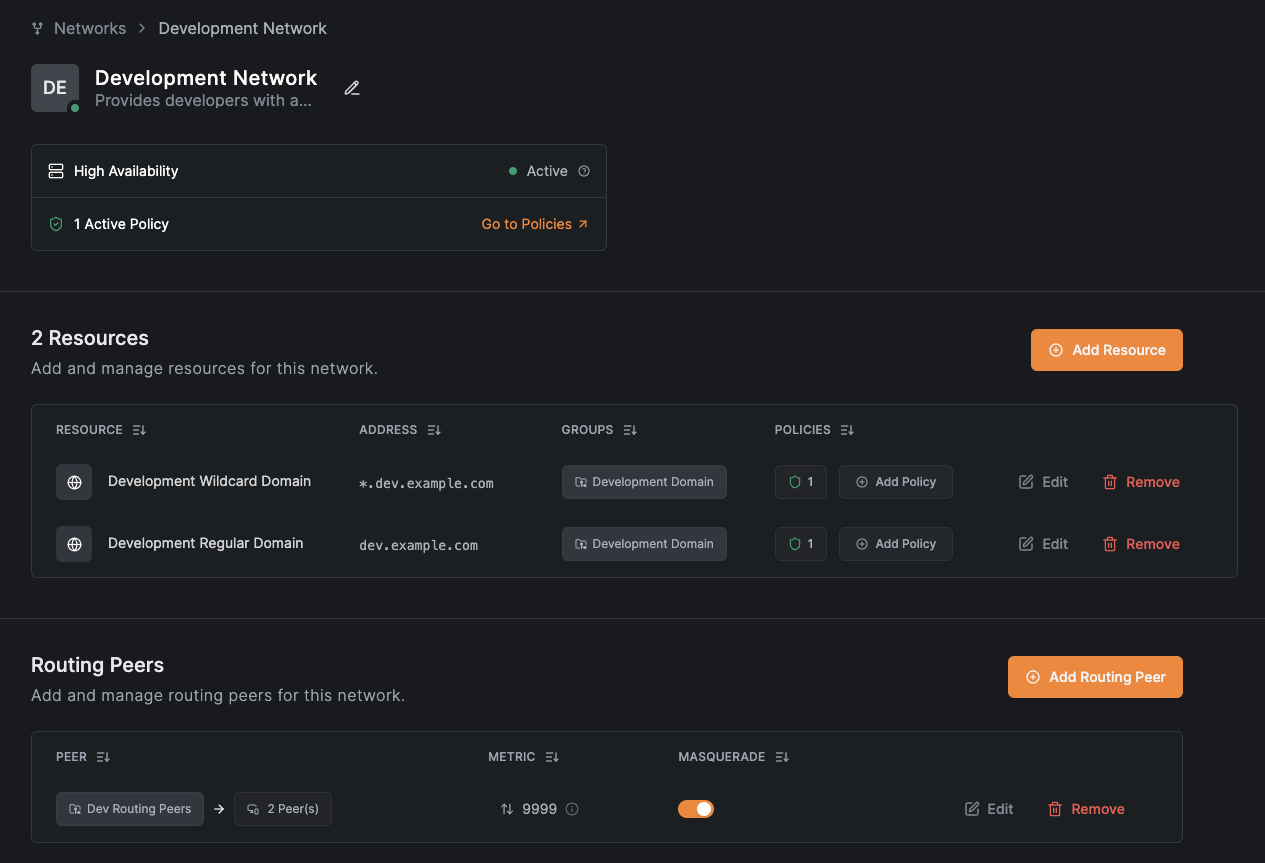
Verify the configuration from a developer workstation:
$ netbird networks ls
Available Networks:
- ID: Development Regular Domain
Domains: dev.example.com
Status: Selected
Resolved IPs:
[example.com]: 93.184.215.14, 2606:2800:21f:cb07:6820:80da:af6b:8b2c
- ID: Development Wildcard Domain
Domains: *.dev.example.com
Status: Selected
Resolved IPs: -
Set up the AI model training network
Follow the same steps to create a network for data scientists.
Create a new network named AI Model Training Network:
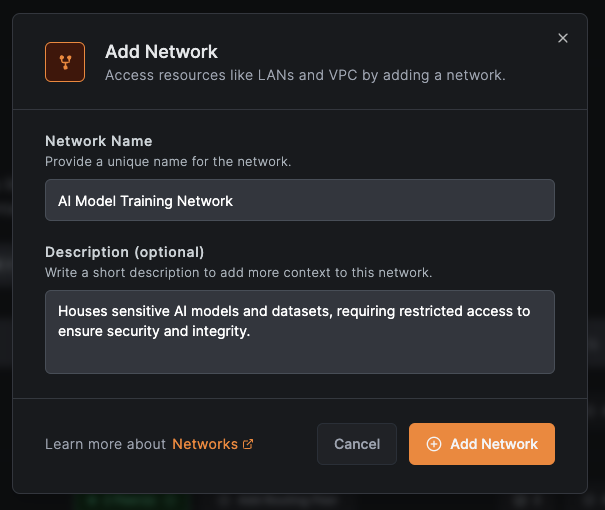
Add routing peers (single or group for high availability):
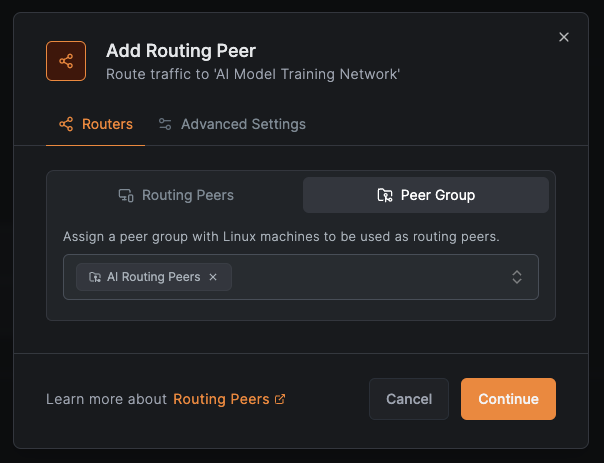
Add the wildcard domain resource for *.ai.example.com:
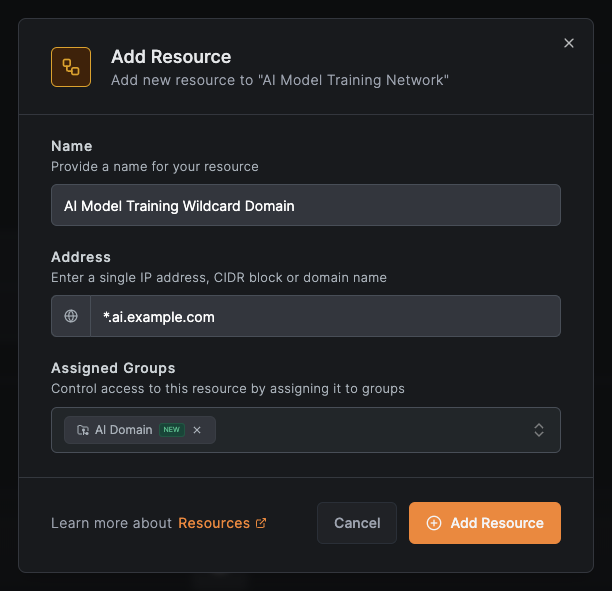
Create an access policy for the Data Scientists group:
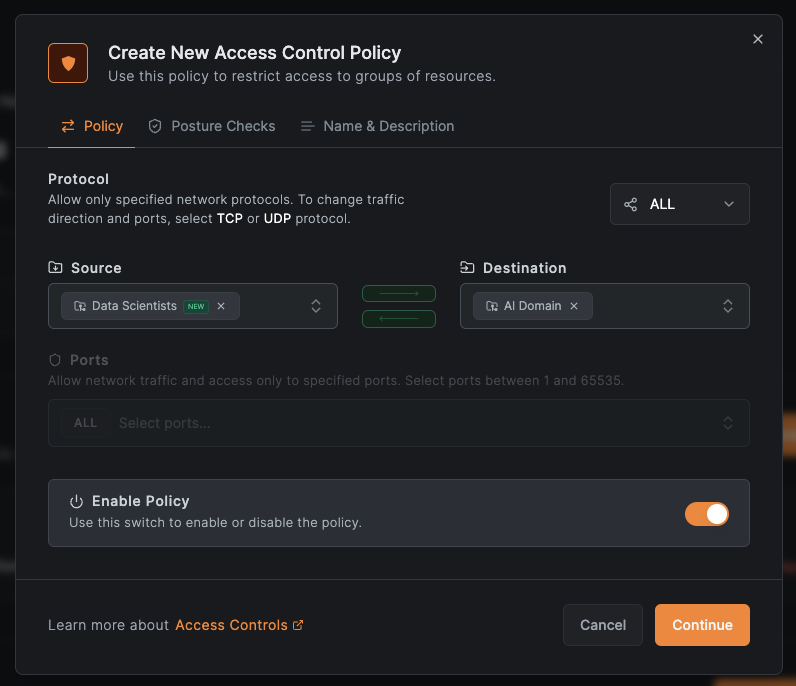
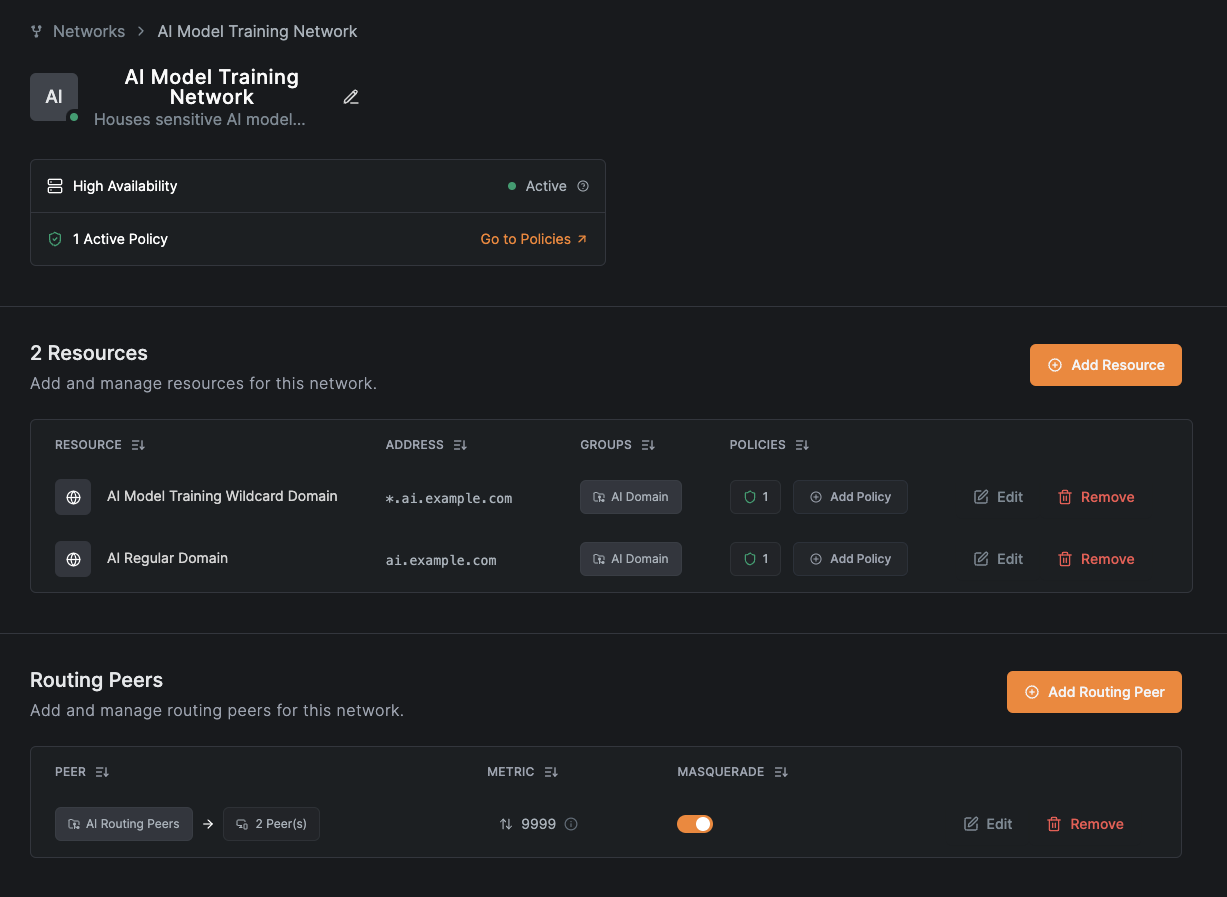
Add the base domain ai.example.com as a separate resource. The completed network:
Add specific subdomain resources
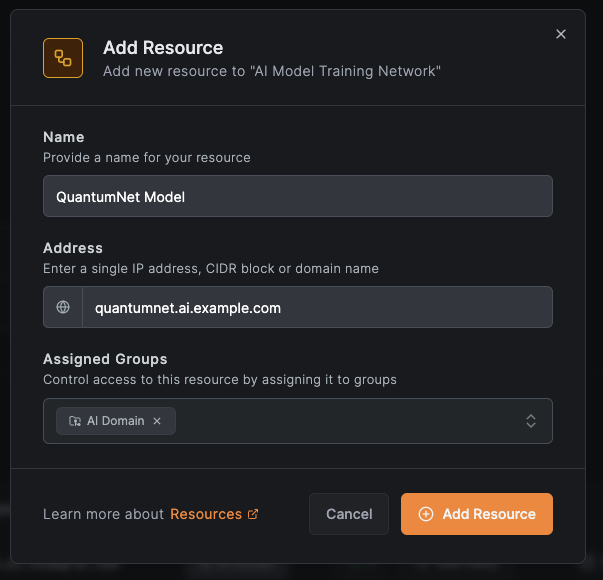
You can add individual subdomain resources for more granular access control. For example, to add a specific AI model subdomain:
Click Add Resource, enter the subdomain name and address, and assign it to the appropriate group:
The network now shows all resources:
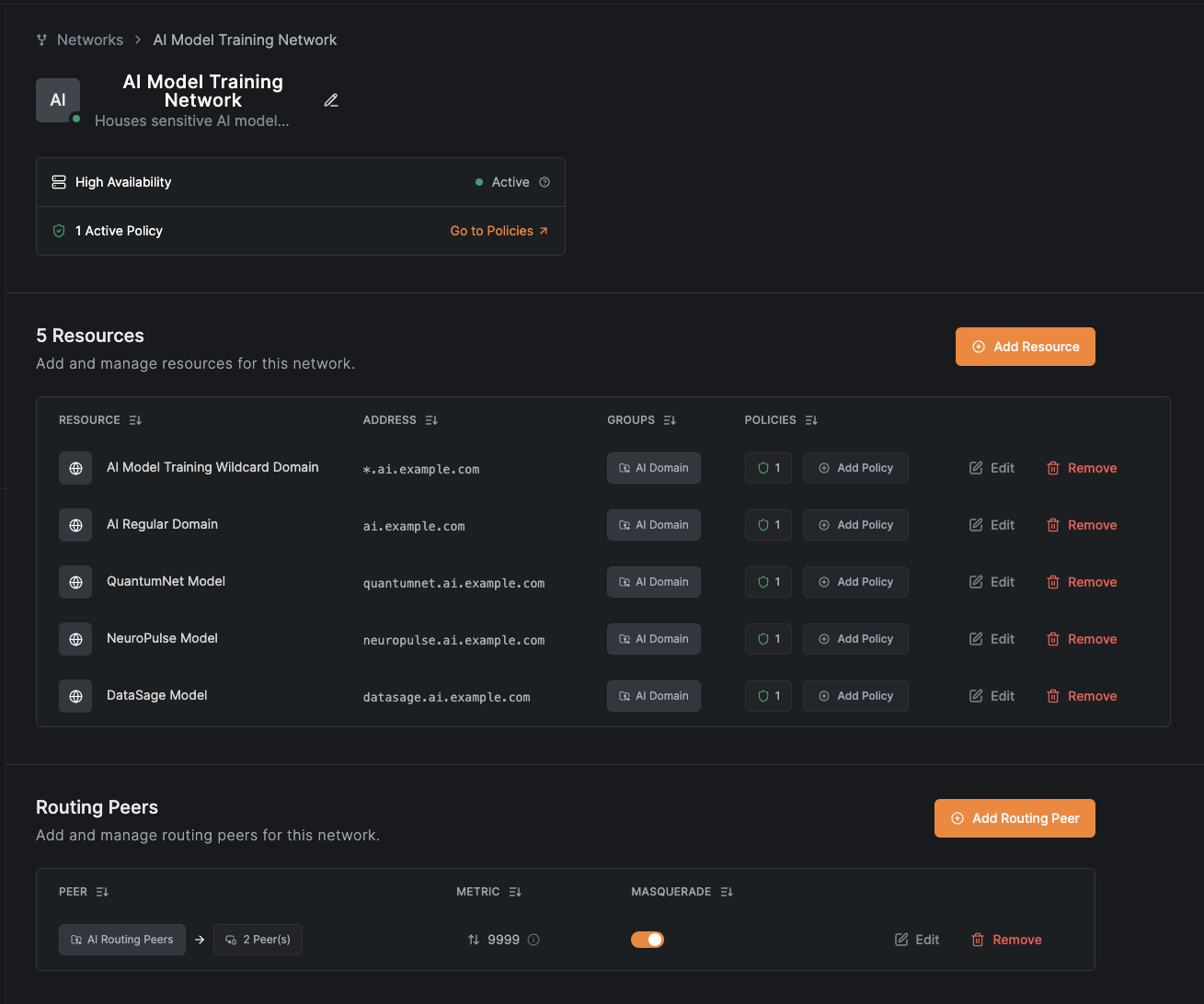
Verify from a data scientist workstation:
$ netbird networks ls
Available Networks:
- ID: AI Model Training Wildcard Domain
Domains: *.ai.example.com
Status: Selected
Resolved IPs: -
- ID: AI Regular Domain
Domains: ai.example.com
Status: Selected
Resolved IPs: -
- ID: DataSage Model
Domains: datasage.ai.example.com
Status: Selected
Resolved IPs: -
- ID: NeuroPulse Model
Domains: neuropulse.ai.example.com
Status: Selected
Resolved IPs: -
- ID: QuantumNet Model
Domains: quantumnet.ai.example.com
Status: Selected
Resolved IPs: -
Data scientists now have access to ai.example.com and all its subdomains. You can create additional access policies for individual subdomains or organize data scientists into teams with different permissions as needed.

