Integrate NetBird with MDM & EDR Platforms
What is EDR and MDM?
Endpoint Detection and Response (EDR) is a cybersecurity technology designed to help organizations detect, investigate, and respond to threats on endpoint devices. An endpoint is any device that is connected to a network, such as laptops, desktops, smartphones, tablets, servers, and even some IoT (Internet of Things) devices.
MDM stands for Mobile Device Management. It's a type of security software that enables organizations to monitor, manage, and secure their employees' mobile devices, including smartphones, tablets, and laptops, across various service providers and operating system.
MDM focuses on managing and securing mobile devices, while EDR focuses on detecting and responding to threats on various endpoints, including desktops, laptops, and servers.
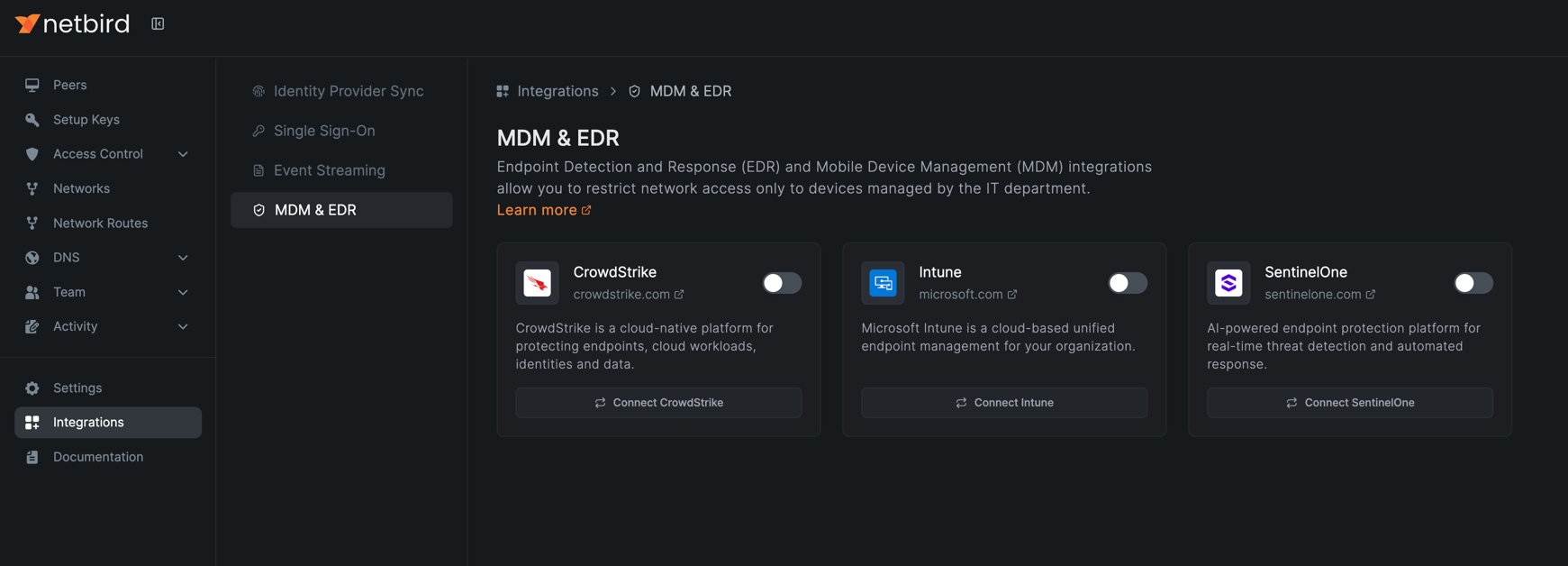
NetBird's EDR and MDM Integration
With the rise of remote work, endpoints often operate outside the traditional corporate network perimeter, making them more vulnerable to attacks. EDR provides a layer of security that is not dependent on the physical location of the endpoint, thus extending protection to remote workers and their devices.
NetBird integrates with major EDR and MDM platforms to restrict network access only to devices managed by the company's IT department. With the integration enabled, NetBird synchronizes the list of devices managed by the MDM or EDR platform via the API and checks the presence of the MDM or EDR agent on the device, blocking access to the network if the agent is not installed or not compliant with the organization's security policies.
NetBird doesn't apply the MDM and EDR checks to all devices in the network. Instead, you can select specific groups of devices for the checks to apply.
This feature is only available in the cloud version of NetBird.
Supported EDR Platforms
NetBird integrates with the following EDR platforms:

