Restrict Network Access with CrowdStrike Falcon®
CrowdStrike Falcon is a cloud-based endpoint protection platform that provides comprehensive visibility and threat detection capabilities. CrowdStrike Falcon agent runs on your devices (endpoints), collects, and analyzes endpoint data to detect and respond to threats in real-time. The agent's presence on endpoints and data it collects can be utilized to enforce access policies and limit network access according to the "health" status of the endpoints.
The integration of NetBird with CrowdStrike Falcon provides organizations with network security controls that allow only IT-managed devices running CrowdStrike to access the network. Additionally, the integration uses CrowdStrike's Zero Trust Assessment (ZTA) score, enabling administrators to further limit network access based on the security posture of each device.
CrowdStrike's Zero Trust Assessment (ZTA) score is a numerical representation of the security posture of a device with a value ranging from 0 to 100. The score is calculated based on various factors, including the device's security configuration, software vulnerabilities, and CrowdStrike's threat intelligence data. By integrating with CrowdStrike Falcon, NetBird can ensure that only devices with a high security posture can access the network.
In this guide, we will walk you through the configuration steps to integrate CrowdStrike Falcon with NetBird and use ZTA score to allow network access to devices that meet a specified ZTA threshold.
Prerequisites
Before you start creating and configuring a CrowdStrike integration, ensure that you have the following:
- A CrowdStrike account with the permissions to create and manage API keys. If you don't have the required permissions, ask your CrowdStrike administrator to grant them to you.
Create a CrowdStrike API Key
- Navigate to the API clients and keys page
- Click
Create API clientat the top, right corner - Set Hosts - Read permission
- Set Zero Trust Assessment - Read permission
- Click
Create - Copy the credentials. You will need these credentials when configuring an integration in NetBird.
Configure a CrowdStrike Integration in NetBird
- Navigate to the Integrations » EDR tab in the NetBird dashboard
- Click
Connect CrowdStriketo start the configuration wizard
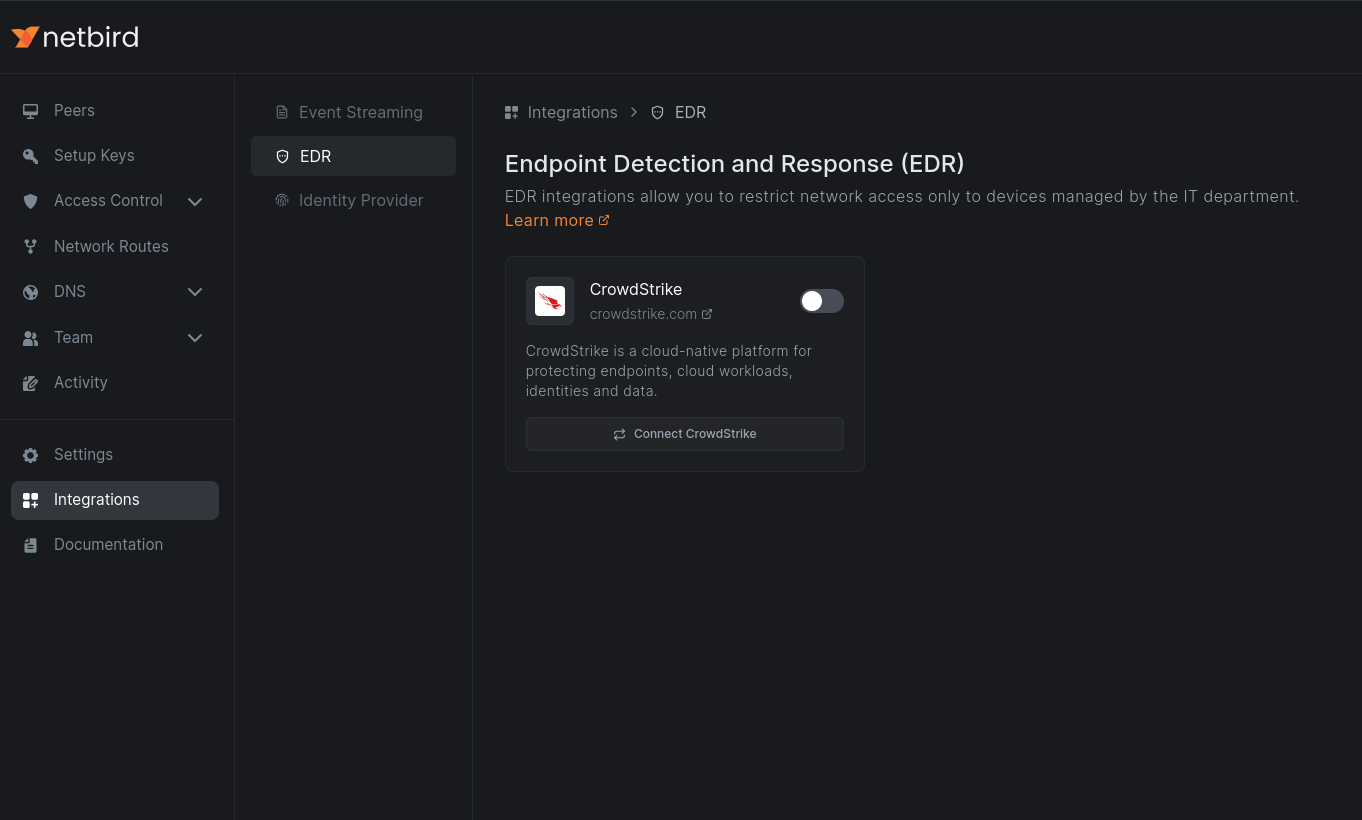
- First, select the region of your CrowdStrike account
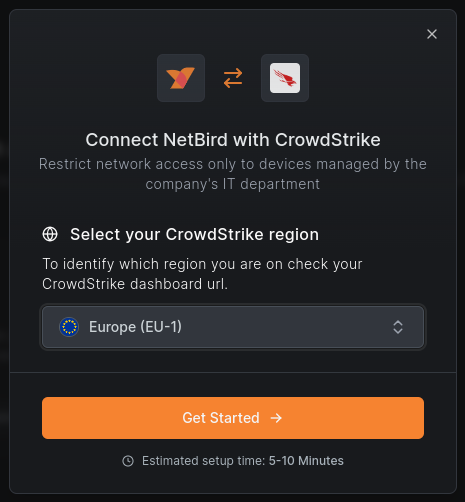
- Then enter the client ID and secret key you created in Step 1 and click
Continue
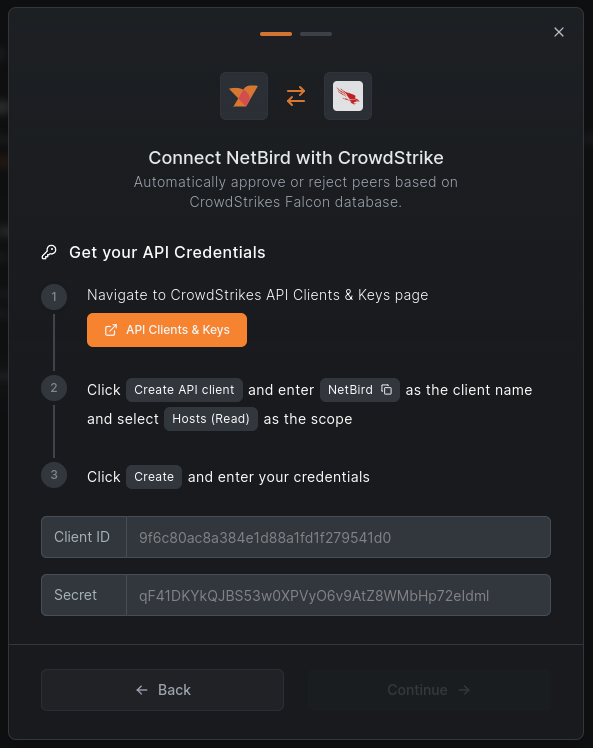
- Select groups you want to apply the integration to
- If you would like to apply a ZTA threshold, then enable the Zero Trust Assessment Score and set the desired limit, and click
Connect.
The EDR check will apply only to machines in the selected groups and will require a running CrowdStrike agent.
You can also use groups synchronized from your Identity Provider (IdP).
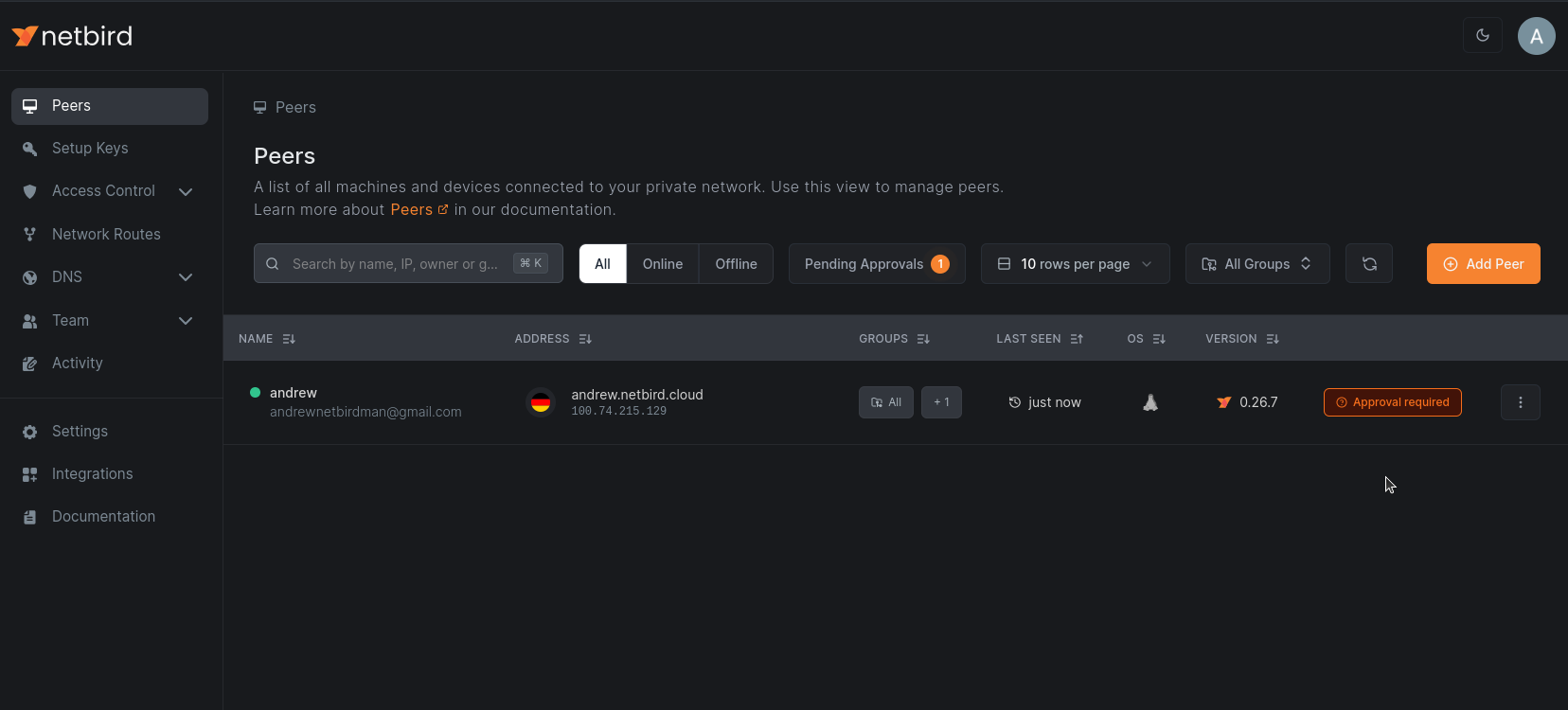
- Peers that have the CrowdStrike agent installed will be granted access to the network. Peers without the agent will appear
with a
Approval requiredmark in the peers list and won't be able to access the network until the agent is installed.
- Optional. You can experiment and see how the integration works by hiding hosts in the CrowdStrike Host management console:
- Navigate to the Host management page in the CrowdStrike console
- Select a host you want to hide
- Click
Actionsand thenHide - The host will be moved to Trash (you can restore it later)
- After about a minute, the peer will be disconnected from the network and marked as
Approval requiredin the NetBird dashboard. - To restore the host in CrowdStrike, navigate to the Trash and click
Restore
NetBird synchronizes the list of devices managed by the EDR platform via the API about every minute. The changes might not be visible immediately.
If you install the CrowdStrike agent on a peer after it joined the network, you will need to disconnect and reconnect
this peer for the Approval required mark to disappear.

