Reverse Proxy Authentication
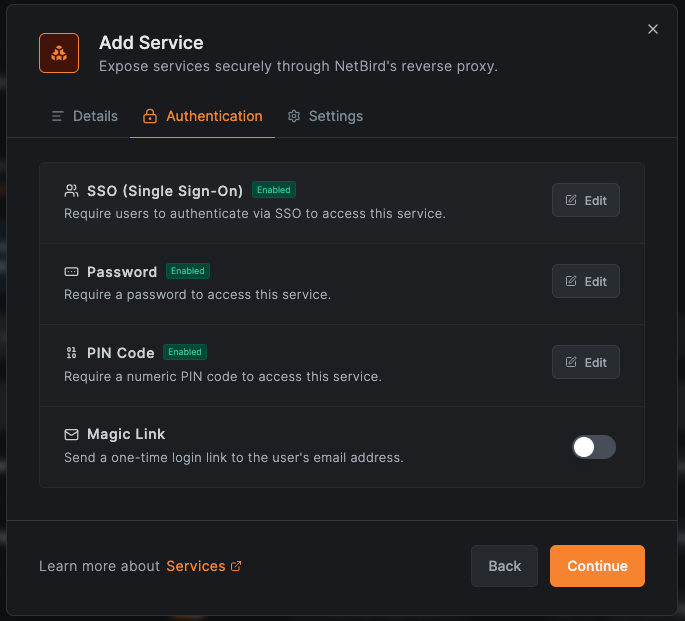
NetBird Reverse Proxy supports multiple authentication methods to control who can access your exposed services. You can enable one or more methods on each service, or leave a service completely public. Authentication is configured per service in the Authentication tab when creating or editing a service.
Authentication methods
NetBird offers three authentication methods, each suited to different access patterns. You can enable any combination of them on a single service.
SSO (Single Sign-On)
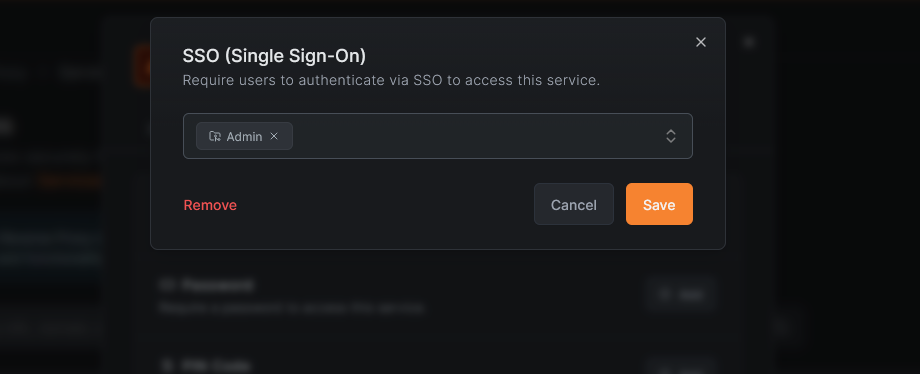
SSO authentication requires users to authenticate through your identity provider (IdP) using OIDC before they can access the service. When a user visits the service URL, they are redirected to your IdP login page. After successful authentication, they are granted access to the service.
You can optionally restrict access to specific distribution groups from your IdP. When groups are configured, only users who belong to at least one of the selected groups are allowed through after authenticating.
Key details:
- Users authenticate via your existing identity provider (OIDC)
- Sessions last 24 hours before re-authentication is required
- Optionally restrict access to specific distribution groups synced from your IdP
- When no groups are selected, any authenticated user in your organization can access the service
Self-hosted deployments: SSO authentication uses whichever OIDC provider is configured in your management server. If you use the built-in embedded IdP, SSO works automatically. If you use an external identity provider (Auth0, Okta, Keycloak, etc.) without the embedded IdP, you must register the reverse proxy callback URL with your IdP before SSO will work. See the Enable Reverse Proxy migration guide for step-by-step instructions.
Best for: Team services where you want to leverage existing identity management, internal tools that require user-level accountability, and services where you need group-based access control.
Password
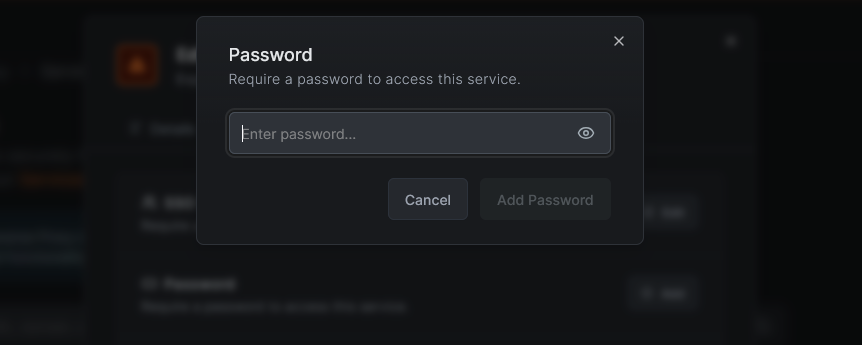
Password authentication protects a service with a shared password that you define. When a user visits the service URL, they are prompted to enter the password before they can proceed. Passwords are securely hashed using Argon2id on the backend - the plaintext password is never stored.
Key details:
- Set a shared password when configuring the service
- Users must enter the correct password to access the service
- Passwords are hashed with Argon2id before being stored
- Sessions last 24 hours before re-authentication is required
Best for: Simple shared access to internal tools, staging environments, or services shared with external partners who do not have accounts in your identity provider.
PIN Code
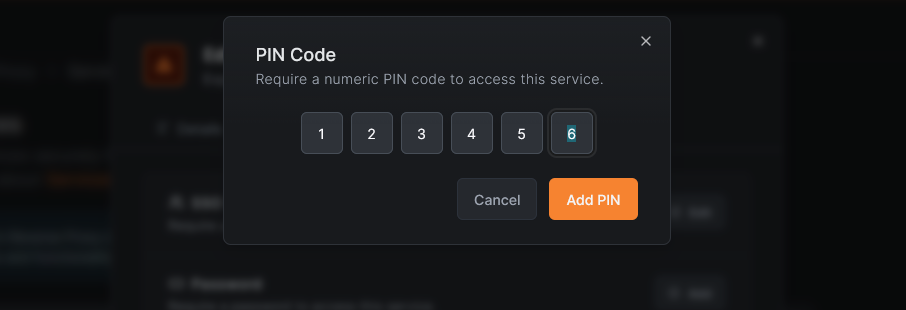
PIN code authentication works similarly to password authentication but is limited to numeric input. When a user visits the service URL, they are prompted to enter the PIN code. PINs are securely hashed using Argon2id on the backend, just like passwords.
Key details:
- Set a numeric PIN code when configuring the service
- Users must enter the correct PIN to access the service
- PINs are hashed with Argon2id before being stored
- Sessions last 24 hours before re-authentication is required
Best for: Quick access scenarios, kiosk-style interfaces, or situations where a simple numeric code is easier to share than a full password.
No authentication (public access)
Services can also be configured without any authentication. When no authentication method is enabled, anyone with the service URL can access it without any restrictions.
When you save a service with no authentication configured, the dashboard displays a warning: "This service will be publicly accessible to everyone on the internet without any restrictions." You must confirm before the service is saved. Make sure this is intentional before proceeding.
Best for: Public-facing websites, APIs that handle their own authentication internally, or services that are intentionally open to the internet.
Combining authentication methods
You can enable multiple authentication methods on a single service simultaneously. When more than one method is active, users can authenticate using any of the enabled methods - they choose which one to use when accessing the service.
For example, you could enable both SSO and Password on the same service. Team members who have accounts in your identity provider can authenticate with SSO, while external partners or contractors can use a shared password. This gives you flexibility without requiring everyone to be in your IdP.
Common combinations include:
| Combination | Use case |
|---|---|
| SSO + Password | Team members use SSO; external collaborators use a shared password |
| SSO + PIN Code | Team members use SSO; quick access via PIN for specific scenarios |
| Password + PIN Code | Different shared credentials for different groups of users |
| SSO + Password + PIN Code | Maximum flexibility with all methods available |
Configuring authentication
All authentication settings are managed in the Authentication tab of the service creation or edit modal. Navigate to Reverse Proxy > Services, then either click Add Service to create a new service or click an existing service to edit it.
Setting up SSO
- Open the service modal (create or edit).
- Switch to the Authentication tab.
- Click SSO (Single Sign-On).
- Enable SSO using the toggle.
- Optionally, select one or more distribution groups to restrict access to specific users. If no groups are selected, all authenticated users in your organization can access the service.
- Click Save (or Save Changes when editing).
Distribution groups are synced from your identity provider. If you do not see the groups you expect, check your IdP sync configuration or Single Sign-On setup.
Setting up a password
- Open the service modal (create or edit).
- Switch to the Authentication tab.
- Click Password.
- Enter a password in the input field.
- Click Save (or Save Changes when editing).
Setting up a PIN code
- Open the service modal (create or edit).
- Switch to the Authentication tab.
- Click PIN Code.
- Enter a numeric PIN in the input field.
- Click Save (or Save Changes when editing).
Removing authentication
To remove an authentication method from a service:
- Open the service modal by clicking the service in the services list.
- Switch to the Authentication tab.
- Click on the authentication method you want to remove.
- Use the Remove option to disable it.
- Click Save Changes.
If you remove all authentication methods, the service becomes publicly accessible. The dashboard will display a warning before saving, as described in the No authentication section above.
Session management
Authenticated sessions for reverse proxy services are managed using JWT (JSON Web Token) technology. Here is how sessions work:
- Token signing: Sessions use JWT tokens signed with Ed25519 key pairs. Each service has its own unique key pair, ensuring that tokens for one service cannot be used to access another.
- Session duration: Authenticated sessions expire after 24 hours. After expiry, users must re-authenticate using whichever method they originally used.
- Scope: Sessions are scoped to individual services. Authenticating with one service does not grant access to other services, even if they use the same authentication method.
Related pages
- Reverse Proxy Overview - learn how the reverse proxy feature works and create your first service
- Custom Domains - configure your own domain names for reverse proxy services
- Access Logs - monitor and audit traffic to your reverse proxy services
- Single Sign-On - configure your identity provider for SSO across NetBird
- Provision Users and Groups - sync users and groups from your identity provider

