Reverse Proxy Access Logs
NetBird logs every request that passes through your reverse proxy services. Access logs provide visibility into who is accessing your services, from where, and whether requests were allowed or denied. This is useful for auditing, debugging, and monitoring traffic to your publicly exposed services.
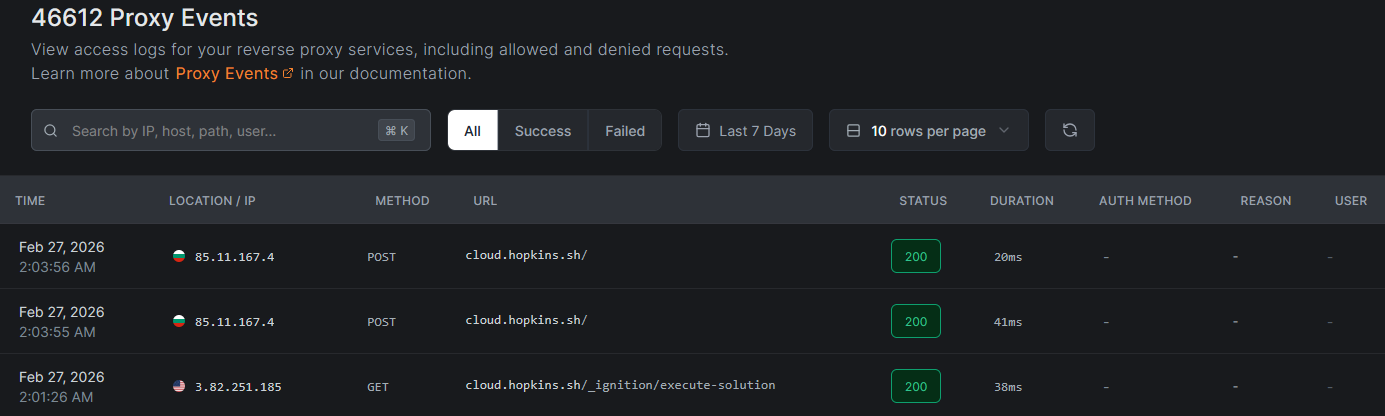
Viewing access logs
Access logs are available in the NetBird dashboard under Activity > Proxy Events. This view displays a table of all HTTP requests that have passed through your reverse proxy services, with filters to narrow down results by time range, status, or other fields.
You can also retrieve access logs programmatically using the API:
GET /api/events/proxy
What access logs capture
Each log entry records the following information about an HTTP request:
| Field | Description |
|---|---|
| Timestamp | When the request occurred |
| Method | HTTP method (GET, POST, PUT, DELETE, etc.) |
| Host | The domain the request was made to |
| Path | The URL path requested |
| Status Code | HTTP status code returned (200, 401, 403, 500, etc.) |
| Duration | How long the request took (in milliseconds) |
| Source IP | The client's IP address |
| Auth Method | Which authentication method was used (SSO, password, PIN, or none) |
| User ID | The authenticated user's ID (if SSO was used) |
| Country | Country of origin based on source IP geolocation |
| City | City of origin based on source IP geolocation |
| Reason | Reason for denial (if applicable) |
Understanding log entries
Log entries fall into three categories based on the HTTP status code returned:
- Allowed requests - Successful requests show a
2xxstatus code along with the authentication method used to access the service. - Denied requests - Failed authentication attempts show
401or403status codes with a reason explaining why the request was denied, such as an invalid password or missing SSO session. - Errors - Backend errors or proxy issues show
5xxstatus codes. These typically indicate that the target service is unreachable or returned an error.
Use cases
Access logs support several operational and security workflows:
- Security auditing - Review who accessed sensitive services, which authentication method they used, and from which geographic locations. This helps identify unauthorized access attempts and verify that authentication policies are working as expected.
- Debugging - Trace failed requests to understand authentication or routing issues. The status code, duration, and reason fields help pinpoint whether problems originate from authentication configuration, target availability, or network connectivity.
- Monitoring - Track usage patterns across your services. Identify which services receive the most traffic, peak usage times, and unusual access patterns that may warrant investigation.
- Compliance - Maintain records of service access for regulatory requirements. Access logs provide an auditable trail of who accessed what, when, and from where.
Related pages
- Reverse Proxy Overview - learn how to create and manage reverse proxy services
- Audit Events Logging - view management-level events such as configuration changes and user activity
- Traffic Events Logging - monitor network-level traffic events across your NetBird mesh

