Routing traffic to multiple IP resources
This guide shows how to route traffic to multiple IP resources using NetBird Networks with IP resources. This is a common scenario for DevOps and Platform teams who need to provide differentiated access to on-premises or cloud infrastructure.
Example scenario
In this example, you will configure access to an internal network (172.16.0.0/15) with these requirements:
- All users need access to DNS servers at
172.16.30.2and172.17.100.2(UDP port 53 only) - The DevOps team needs full access to the entire network range
Traffic will be routed through routing peers running inside the network.
Create a network
Navigate to Networks > Networks in the NetBird dashboard:
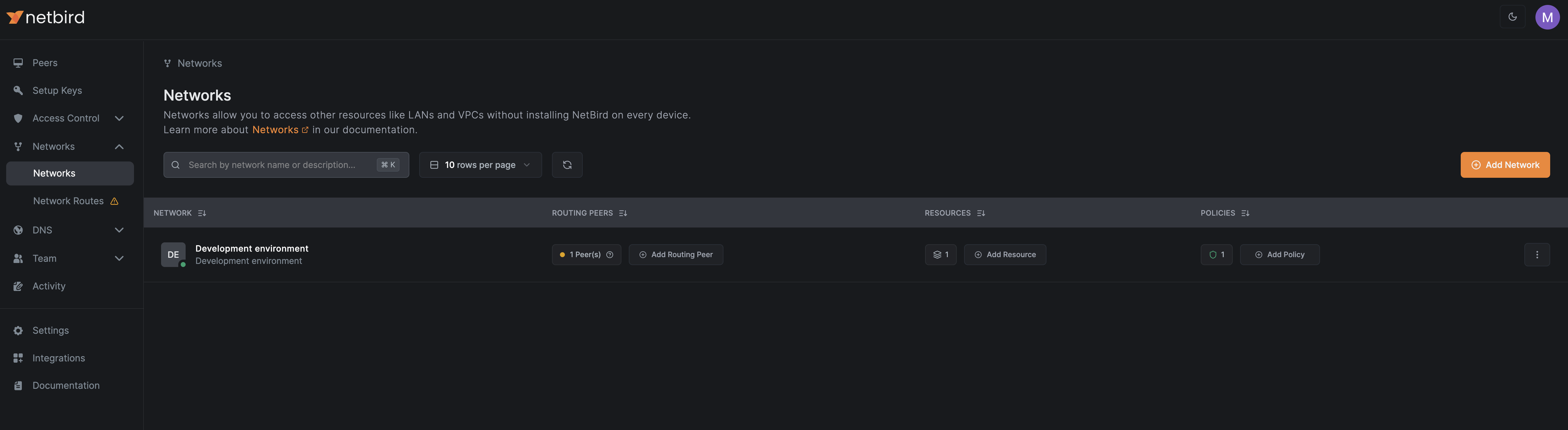
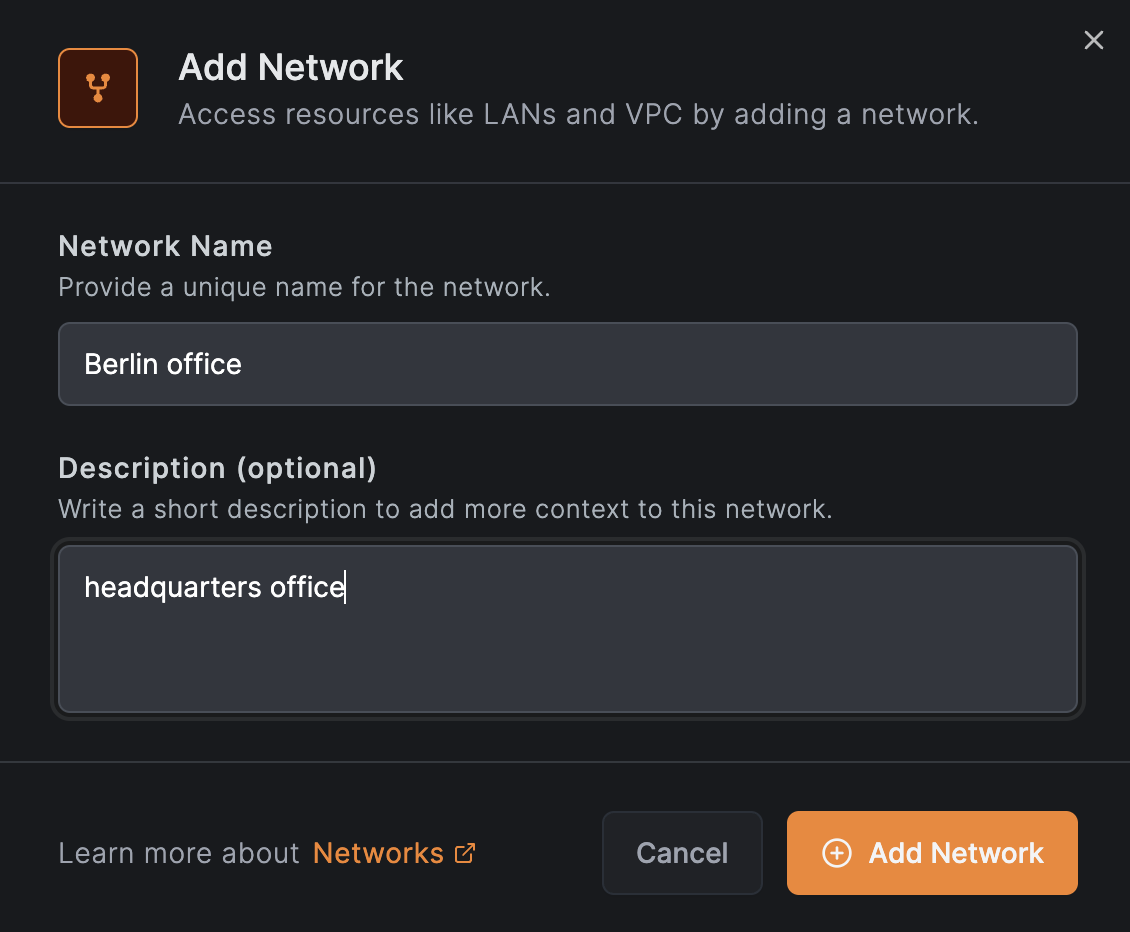
Click Add Network to open the setup wizard. Enter a name and description for the network, then click Continue:
Add a routing peer
Click Add routing peer and select a peer from your network:
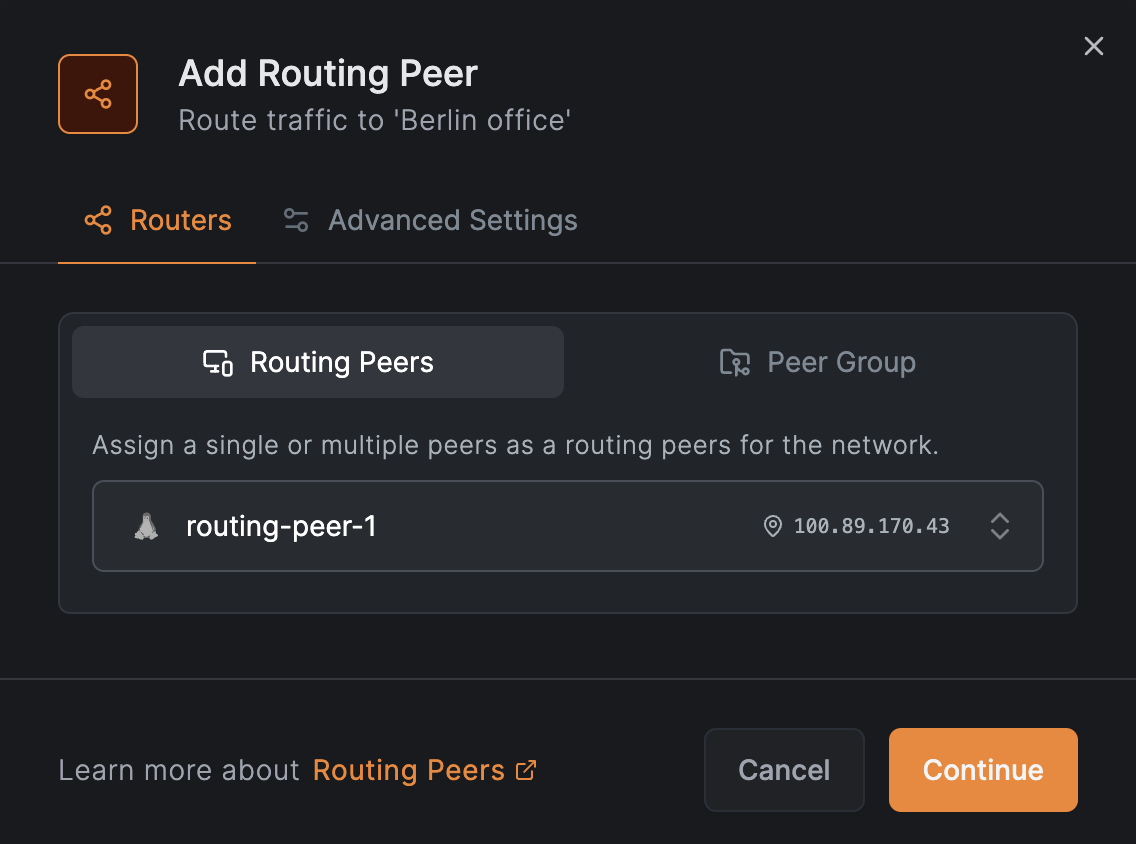
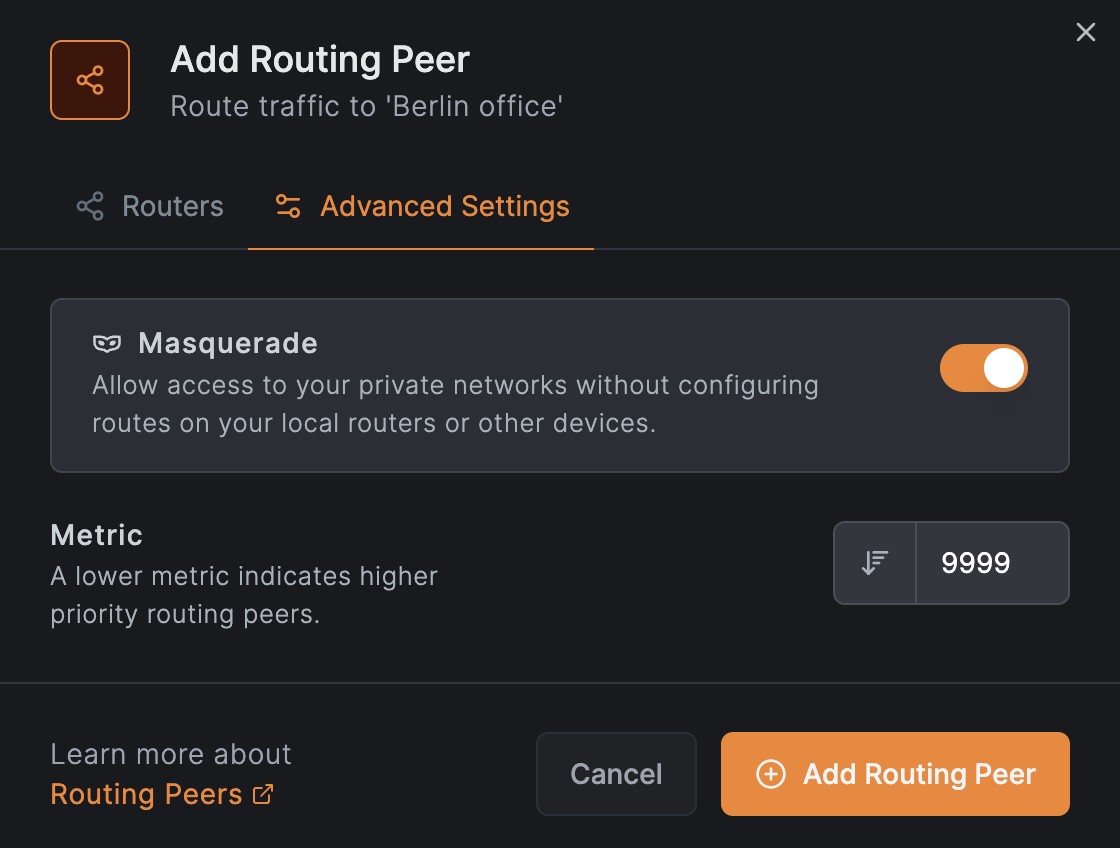
Click Continue, then accept the defaults and click Add Routing Peer:
Add the network resource
Click Add Resource and enter Office network as the name with IP range 172.16.0.0/15 as the address:
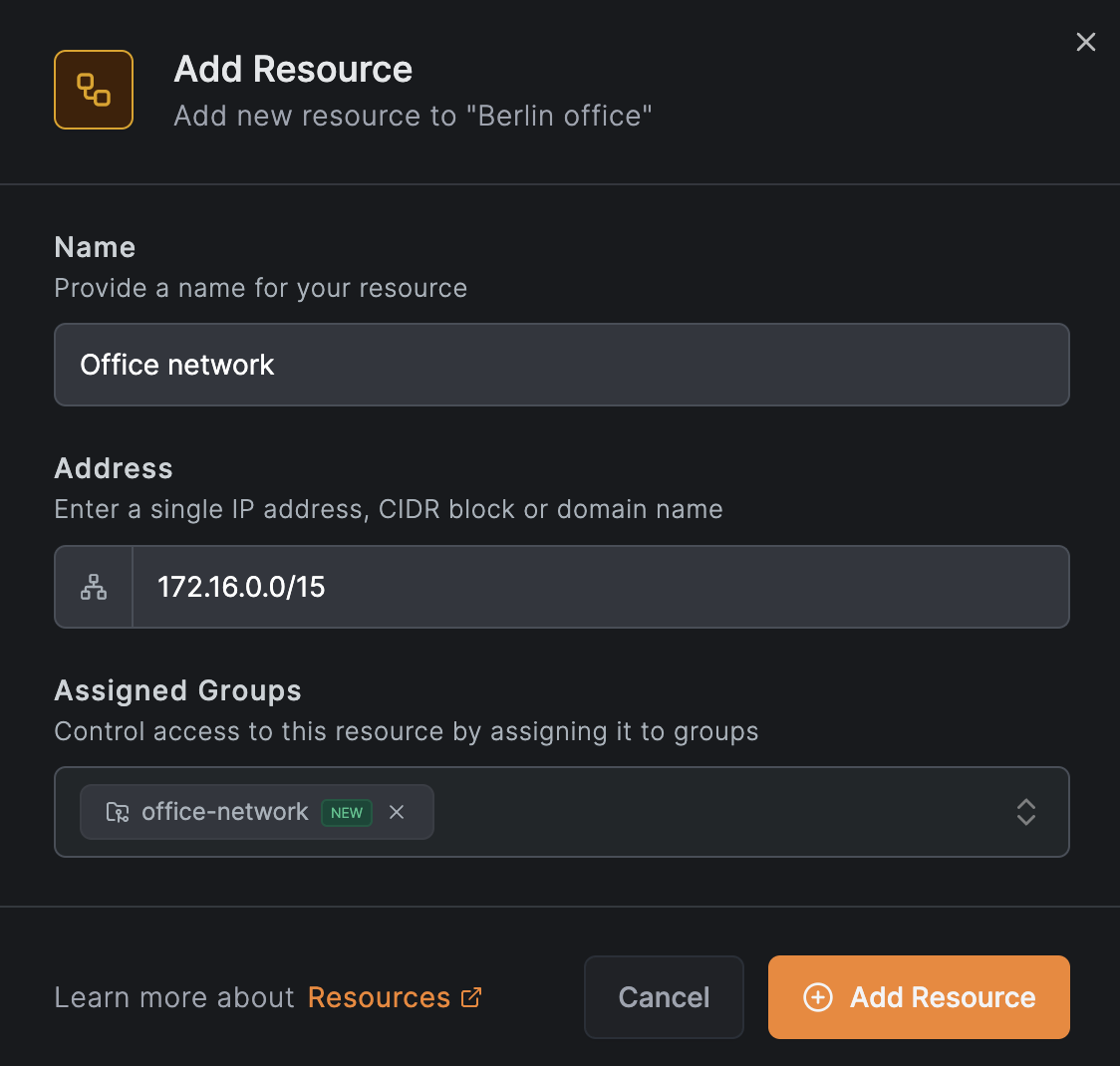
Assign the group office-network to this resource. This group will be used in the access policy for the DevOps team.
Create an access policy for the network resource
Create a policy that grants the DevOps group full access to the office-network resource group.
Click Create Policy and configure the fields as shown:
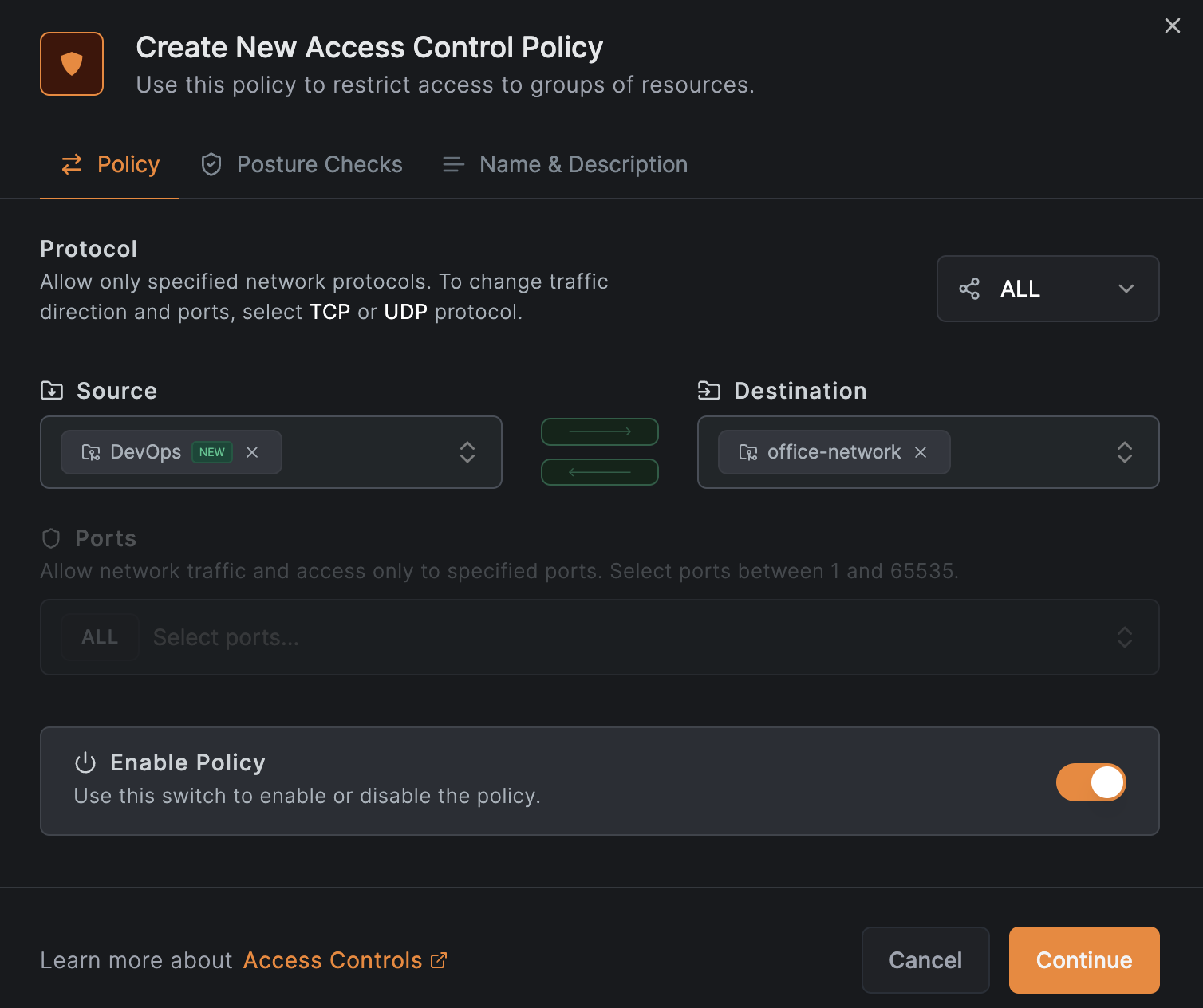
Click Continue twice, then click Add Policy:
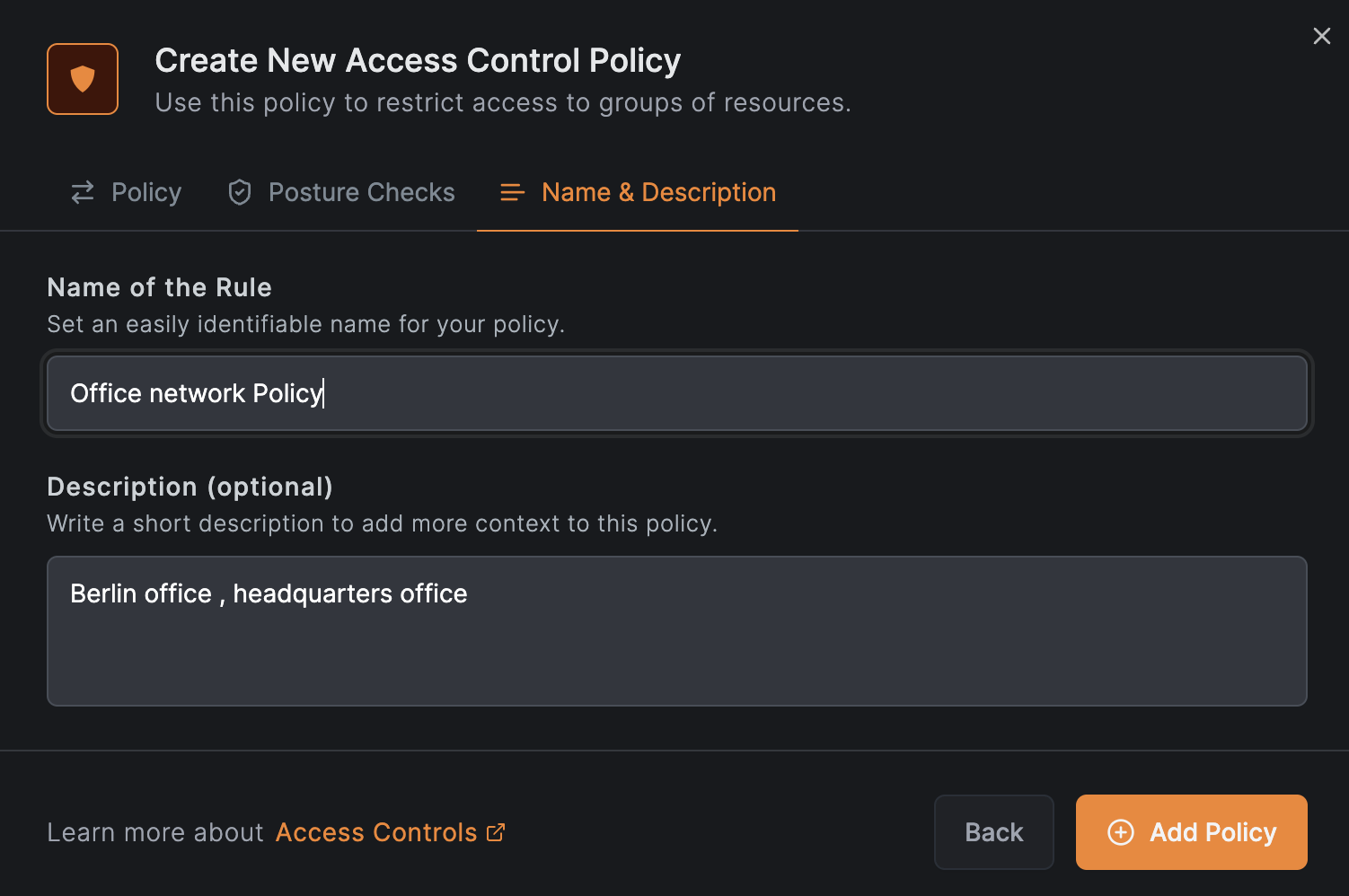
Add the DNS server resources
Add the first DNS server as a resource. Click Add Resource and enter the IP address:
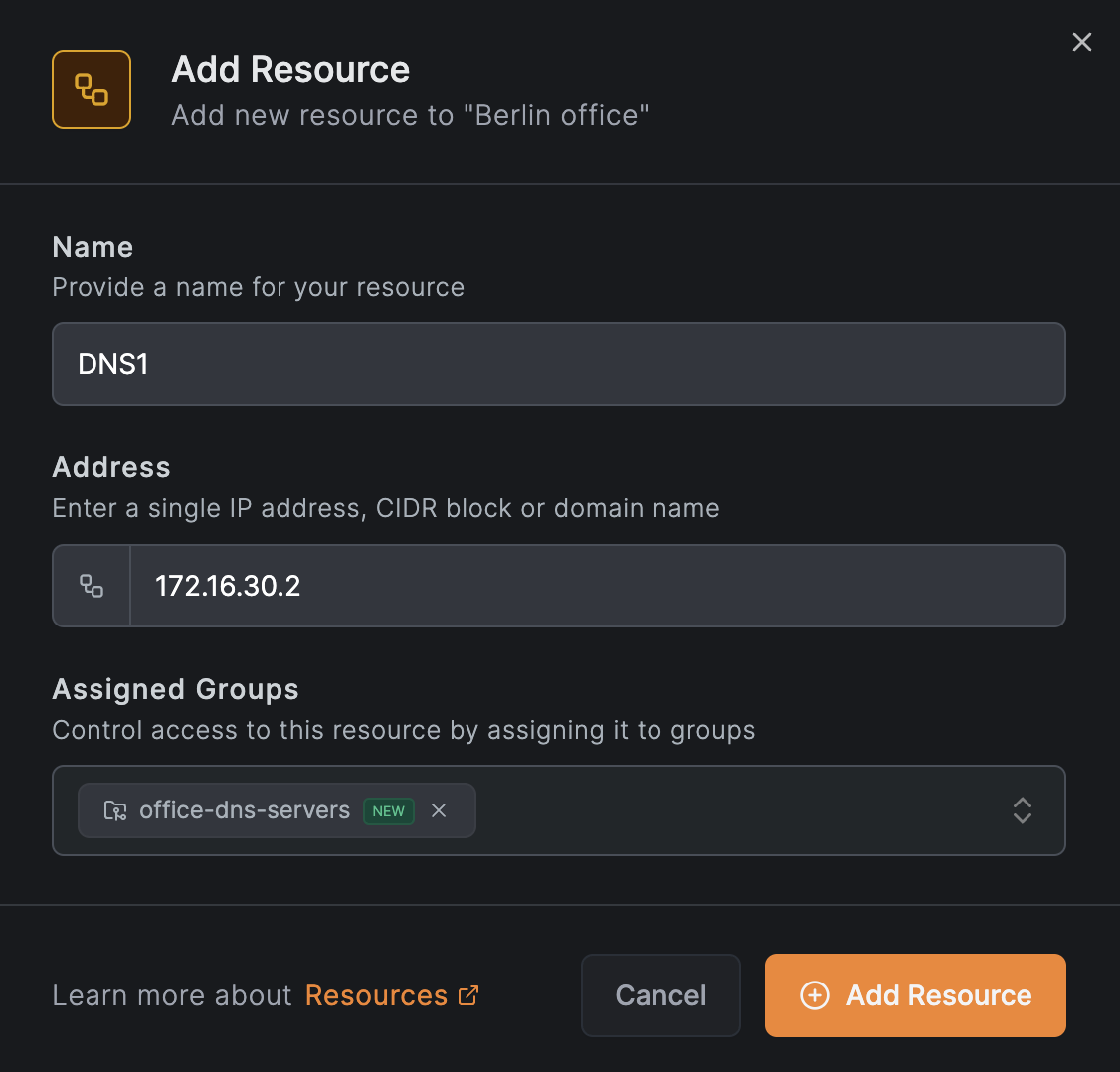
Assign the group office-dns-servers to this resource. When prompted to create a policy, click Later since you will add another DNS server first.
Add the second DNS server resource:
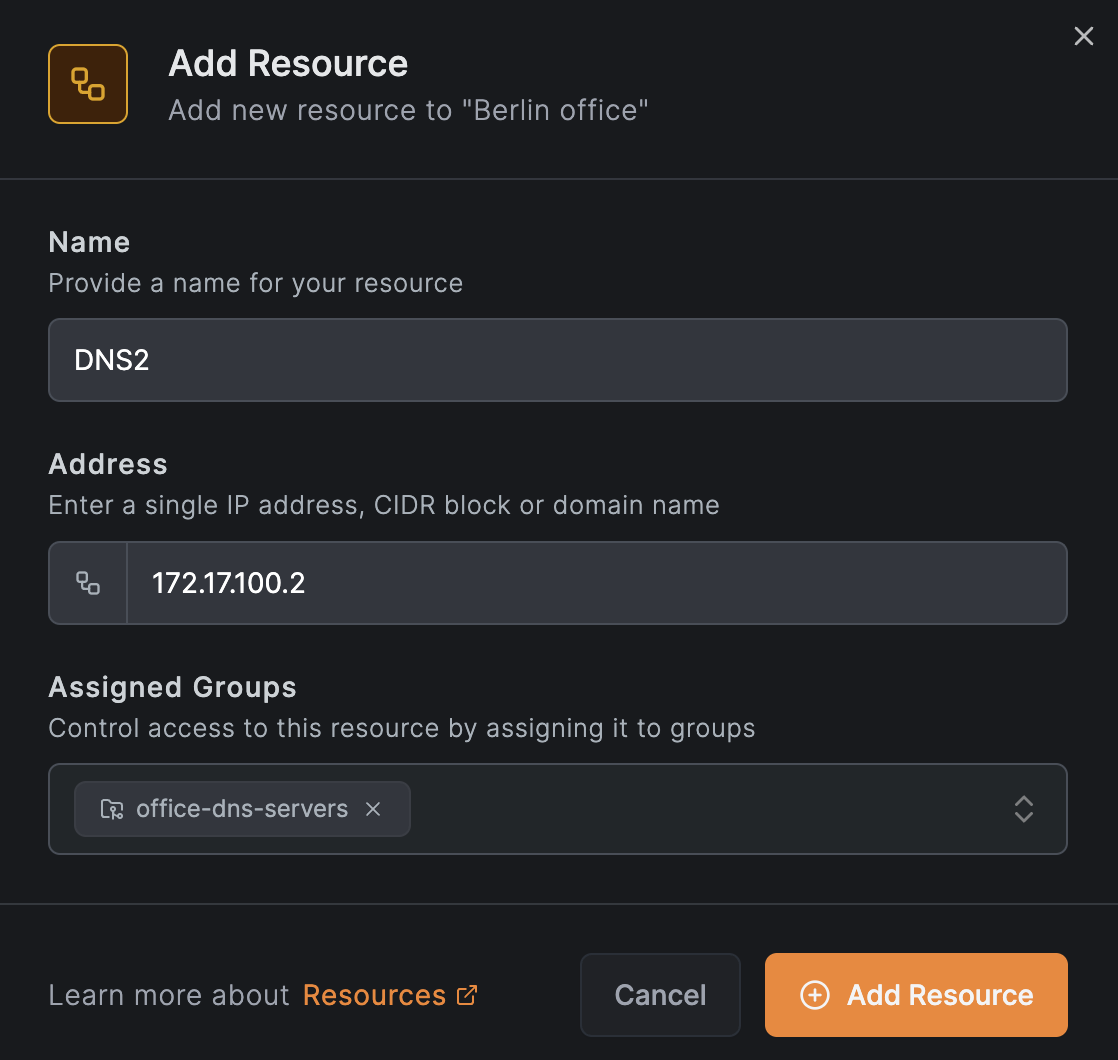
Create an access policy for DNS servers
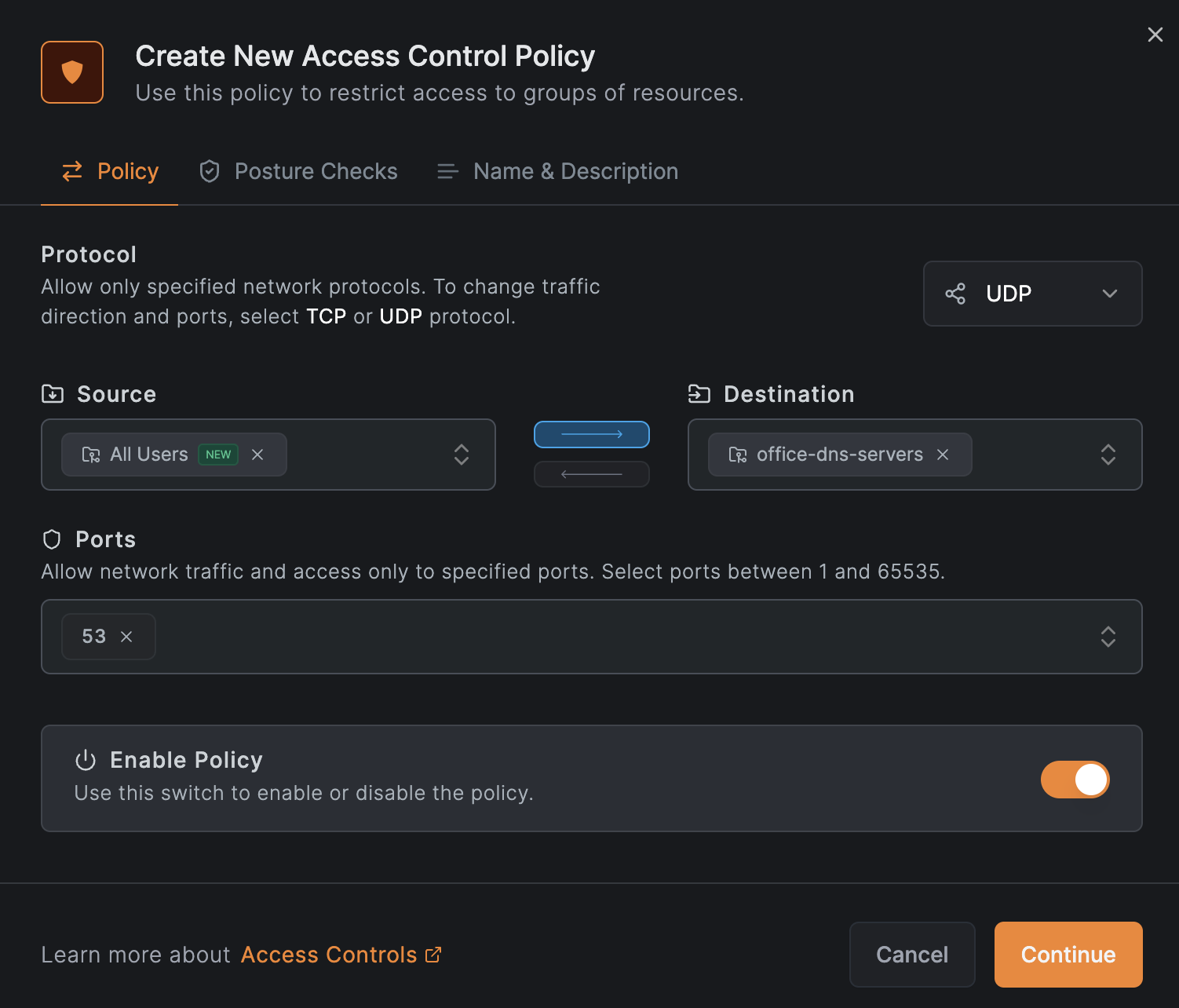
Create a policy that grants the All users group access to the office-dns-servers resource group on UDP port 53 only.
Click Create Policy and configure the fields:
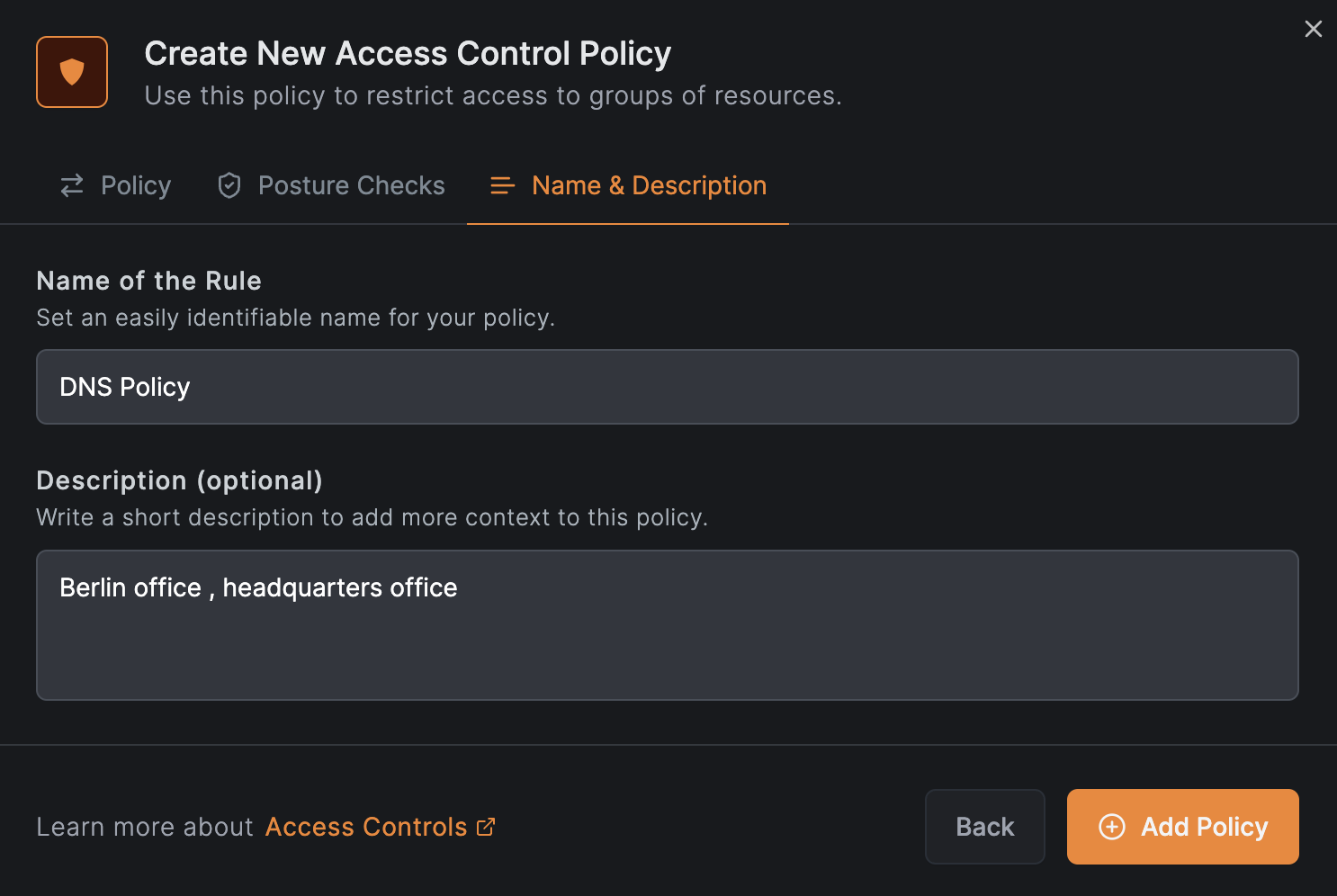
Click Continue twice, then click Add Policy. Use a generic policy name to cover both DNS server addresses:
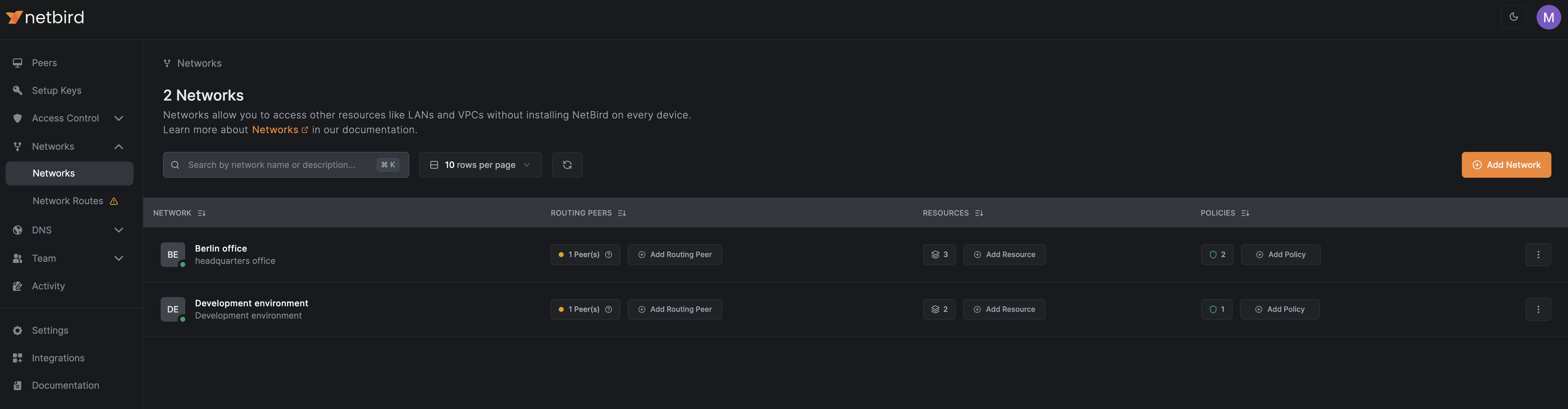
View the network
After completing the wizard, the network appears in the Networks list:
Click the network name to view details:
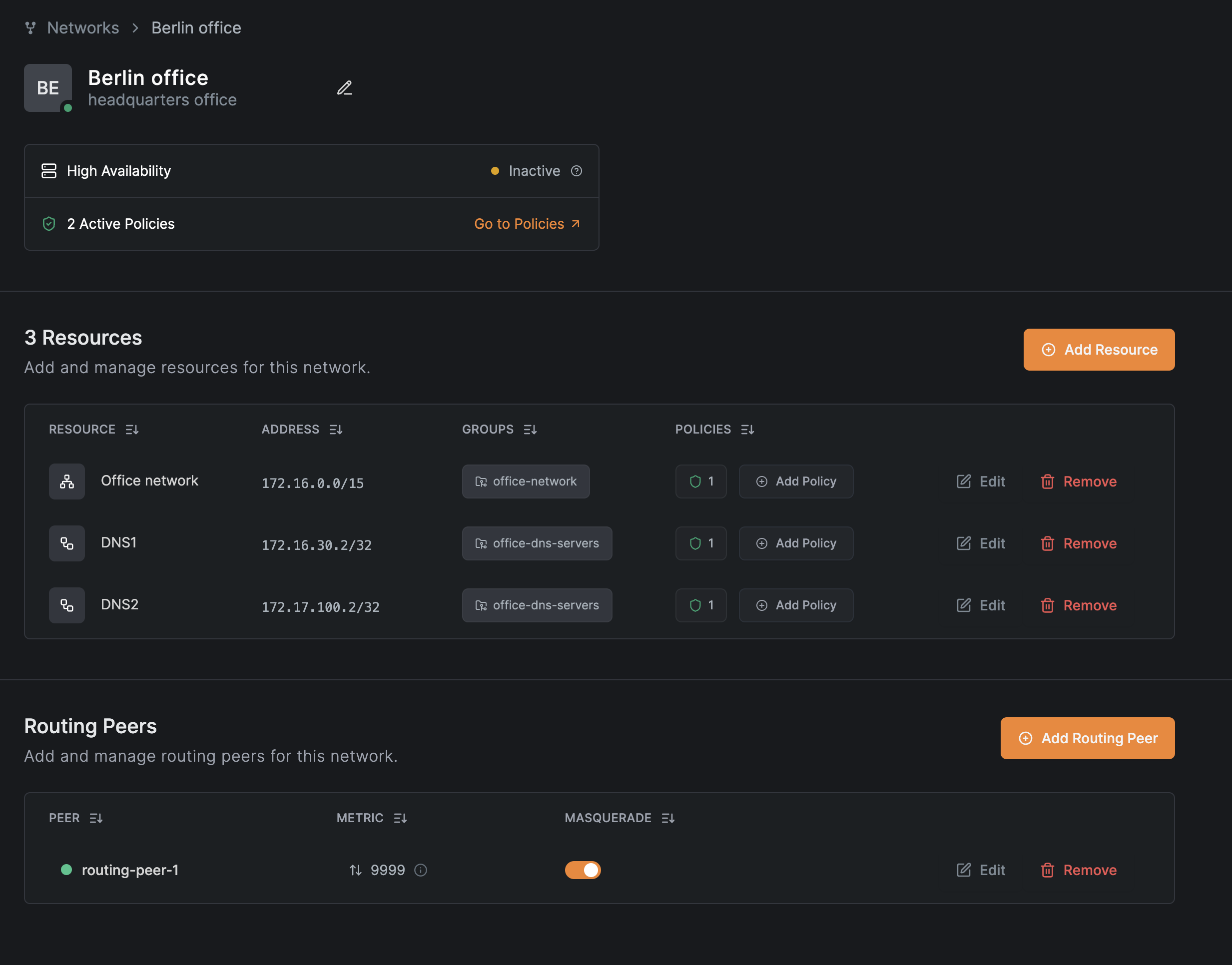
From this view, you can edit or add resources and routing peers using the Edit buttons in each section.
You have now created a network with multiple resources that provide different access levels to different user groups within your organization.
Get started
- Make sure to star us on GitHub
- Follow us on X
- Join our Slack Channel
- NetBird latest release on GitHub

