Configuring Nameservers
Nameservers let you control which DNS servers your peers use and which domains they handle. This guide walks you through common configuration scenarios.
In the NetBird UI, these are called Nameservers. In the API documentation, they're referred to as "nameserver groups" because each configuration can contain multiple DNS server IPs for redundancy.
Before You Start
Make sure you understand:
- DNS basics and how NetBird handles DNS
- Which domains you want to resolve privately vs. publicly
- The IP addresses of your DNS servers
Creating Your First Nameserver
The nameserver configuration follows a step-by-step UI flow with three tabs:
- Nameserver (required first) - Add DNS server IPs and distribution groups
- Domains (unlocks after step 1) - Configure primary or match domain mode
- Name & Description (unlocks after step 1) - Add descriptive information
The Domains and Name & Description tabs remain disabled until you configure at least one nameserver IP and one distribution group in the Nameserver tab.
Step 1: Choose a DNS Provider
- Log in to the NetBird dashboard
- Navigate to DNS > Nameservers in the left sidebar
- Click Add Nameserver
- Select from predefined providers or choose Custom DNS to use your own
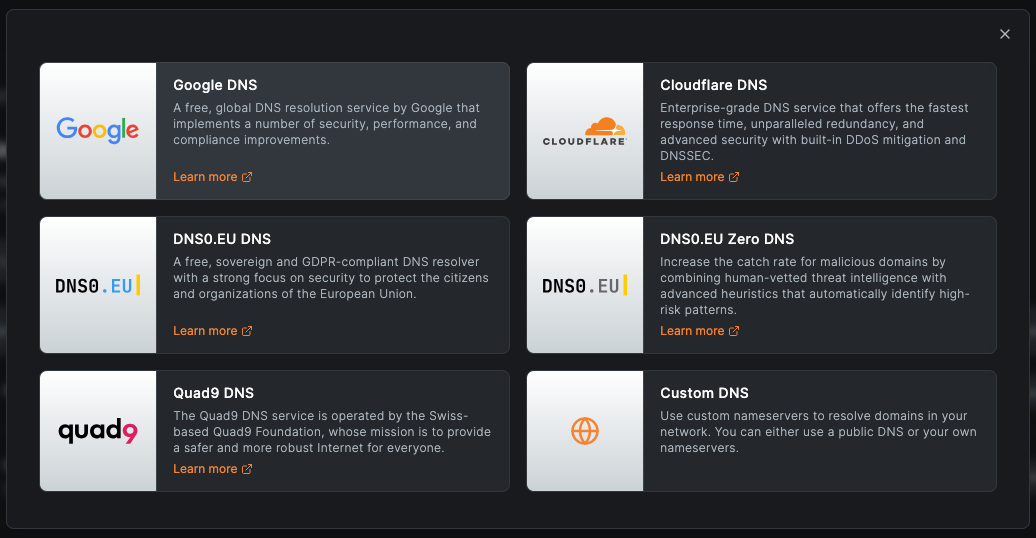
If you choose a predefined provider, the addresses are pre-filled for you.
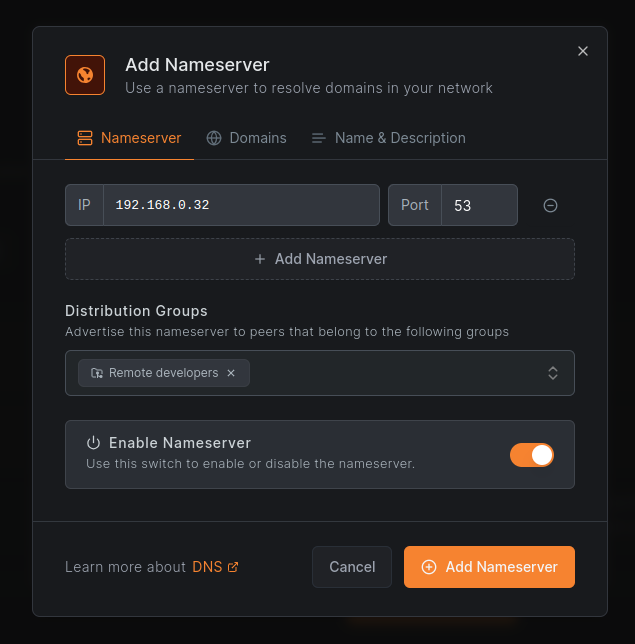
Step 2: Configure Nameserver IPs and Distribution Groups (Nameserver Tab)
After selecting a provider, you'll be on the Nameserver tab. This is the first required step.
Must complete this tab first: You must configure at least one nameserver IP and at least one distribution group before you can access the Domains and Name & Description tabs.
Add Nameserver IPs
Add a nameserver IP (or multiple IPs for redundancy):
- Name
IP- Type
- string
- Required
- required
- Enum
- Description
IP address of the DNS server (e.g.,
10.0.0.1or1.1.1.1)
- Name
Port- Type
- integer
- Required
- required
- Enum
- Description
DNS port, typically
53
Example configuration:
{
"nameservers": [
{"ip": "1.1.1.1", "port": 53},
{"ip": "1.0.0.1", "port": 53}
]
}
Best practice: Configure 2-3 nameservers for redundancy. If the first fails, peers automatically try the next one.
Assign Distribution Groups
Select which peer groups will use this nameserver.
- Name
Distribution Groups- Type
- string[]
- Required
- required
- Enum
- Description
At least one peer group must be selected. All peers in these groups will receive this DNS configuration.
Click + Add Distribution Group and select one or more groups from the dropdown.
Enable/Disable Nameserver
Use the Enable Nameserver toggle to activate or deactivate this configuration without deleting it.
Step 3: Configure Domains (Domains Tab - Optional)
Once nameserver IPs and distribution groups are set, click Continue or navigate to the Domains tab.
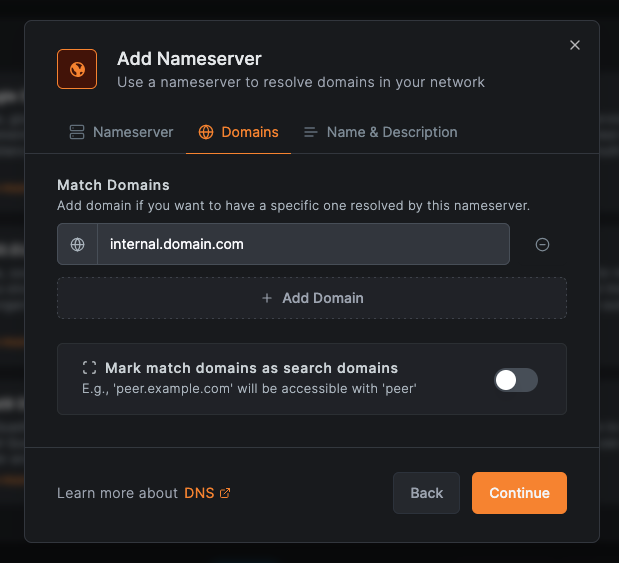
Here you choose whether this is a primary nameserver (handles all domains) or a match domain nameserver (handles specific domains only).
Option A: Primary Nameserver (Leave Domains Empty)
Leave the Match Domains section empty for a primary nameserver that handles all DNS queries not matched by other nameservers.
Important:
- Each peer should have exactly ONE primary nameserver
- Primary nameserver = empty match domains list
- Handles all queries not matched by other nameservers
- If you don't configure a primary, peers use their original DNS settings
Option B: Match Domain Nameserver (Add Specific Domains)
Add specific domains that this nameserver should handle:
Click + Add Domain and enter domain patterns:
Supported patterns:
- Domain match:
company.internal(automatically matches the domain and all its subdomains likeapp.company.internal) - Multiple domains per nameserver
Example for internal DNS:
company.internal
internal.example.com
Adding a domain like company.internal automatically matches both the domain itself and all subdomains (e.g., app.company.internal, server.company.internal). Wildcard syntax (*.domain.com) is not supported in the UI.
Search Domains
Toggle Mark match domains as search domains to enable domain suffix searching.
When enabled:
- Typing
serverexpands toserver.company.internal - Short names automatically try configured domains
- Only applies to match domain nameservers (not primary)
Step 4: Set Name and Description (Name & Description Tab)
Once nameserver IPs and distribution groups are configured, navigate to the Name & Description tab.
- Name
DNS Name- Type
- string
- Required
- required
- Enum
- Description
A descriptive name for this nameserver (e.g., "Cloudflare DNS" or "Internal DNS")
- Name
Description- Type
- string
- Required
- optional
- Enum
- Description
Optional notes about this nameserver's purpose (e.g., "Cloudflare DNS Servers" or "Berlin office resolver for remote developers")
Step 5: Save and Verify
- Click Continue to move through the tabs, or Add Nameserver when you're done configuring
- The nameserver will be created and distributed to the selected peer groups
- Wait 10-30 seconds for peers to receive the update
- Test DNS resolution (see Troubleshooting)
Common Configuration Scenarios
Scenario 1: Simple Internal DNS
Goal: Use Cloudflare for internet, internal DNS for company.internal and all its subdomains
Configuration:
Nameservers
{
"name": "Cloudflare DNS",
"description": "Public internet DNS",
"nameservers": [
{"ip": "1.1.1.1", "ns_type": "udp", "port": 53},
{"ip": "1.0.0.1", "ns_type": "udp", "port": 53}
],
"enabled": true,
"primary": true,
"domains": [],
"search_domains_enabled": false,
"groups": ["All Peers"]
}
Result:
google.com→ Cloudflare (1.1.1.1)app.company.internal→ Internal DNS (10.0.0.1)server→ Expanded toserver.company.internal→ Internal DNS
Scenario 2: Multi-Cloud Environment
Goal: Different DNS for AWS, GCP, Azure, and on-premise
Configuration:
Nameservers
{
"name": "Google Public DNS",
"primary": true,
"domains": [],
"nameservers": [
{"ip": "8.8.8.8", "ns_type": "udp", "port": 53}
],
"groups": ["All Peers"]
}
Scenario 3: Content Filtering for Mobile Devices
Goal: Block ads/malware on company phones and tablets
Configuration:
{
"name": "NextDNS Filtering",
"description": "Content filtering for mobile",
"nameservers": [
{"ip": "45.90.28.0", "ns_type": "udp", "port": 53}
],
"primary": true,
"domains": [],
"groups": ["Mobile Devices"]
}
You can use services like:
- NextDNS: Custom filtering policies
- Quad9: Malware blocking (9.9.9.9)
- CleanBrowsing: Family-safe filtering
- Pi-hole: Self-hosted ad blocking
Scenario 4: Different DNS for Different Teams
Goal: Developers get internal DNS, guests only get public DNS
Configuration:
-
For Developers:
- Primary: Public DNS (all domains)
- Match: Internal DNS (company.internal)
- Assigned to: "Developers" group
-
For Guests:
- Primary: Public DNS only
- No internal DNS access
- Assigned to: "Guests" group
Advanced Configuration
DNS Failover and Redundancy
Always configure multiple nameservers:
{
"nameservers": [
{"ip": "10.0.0.1", "ns_type": "udp", "port": 53}, // Primary
{"ip": "10.0.0.2", "ns_type": "udp", "port": 53}, // Secondary
{"ip": "8.8.8.8", "ns_type": "udp", "port": 53} // Fallback to public
]
}
The client will try servers in order with automatic failover.
Overlapping Domain Patterns
If multiple nameservers match a query, the most specific match wins:
Query: app.us-east.company.internal
Nameservers:
1. company.internal → DNS1
2. us-east.company.internal → DNS2
Result: Uses DNS2 (more specific)
Disabling DNS Management for Specific Groups
Some peers may need to keep their local DNS configuration (e.g., VPN requirements, corporate policy). See DNS Settings to disable DNS management for specific groups.
Updating Nameservers
Editing an Existing Nameserver
- Navigate to DNS → Nameservers
- Click the group to edit
- Modify settings
- Click Save
Changes propagate to peers within 10-30 seconds. No peer restart required.
Temporarily Disabling a Nameserver
Instead of deleting, you can disable:
- Edit the nameserver
- Toggle Enable Nameserver to OFF
- Save
Peers will stop using this nameserver but the configuration is preserved.
Deleting a Nameserver
Before deleting a primary nameserver: Create a new primary first, or peers will revert to their original DNS settings.
- Click the nameserver
- Click Delete
- Confirm deletion
Best Practices
1. Start Simple
Begin with just two nameservers:
- One primary (public DNS)
- One match domain (internal)
Add complexity only as needed.
2. Use Descriptive Names
Bad: "DNS1", "Group A"
Good: "Internal Corporate DNS", "AWS VPC Resolver"
3. Always Have a Primary
Every peer should receive at least one primary nameserver, or they'll use unmanaged DNS.
4. Test in Stages
- Create nameserver
- Assign to a test distribution group first
- Verify DNS works on test peers
- Roll out to all peers
5. Document Your Domains
Keep a list of which domains belong to which systems:
company.internal → On-premise Active Directory (includes all subdomains)
corp.company.internal → Corporate services (includes all subdomains)
ec2.internal → AWS VPC (includes all subdomains)
compute.internal → GCP (includes all subdomains)
6. Monitor and Maintain
- Check that all nameserver IPs are reachable
- Update IP addresses if infrastructure changes
- Remove unused nameservers to keep configuration clean
Verifying Configuration
After creating nameservers, verify they're working:
Check Peer Status
- Go to Peers in dashboard
- Find a peer in your distribution group
- Check DNS status indicator
Test from Peer
On the peer device:
# Check NetBird DNS is active
nslookup example.com 127.0.0.1
# Test internal domain resolution
nslookup internal.company.internal
# Check search domains
ping server # Should expand to server.company.internal
See Troubleshooting for more diagnostic commands.
Next Steps
- Private DNS Behind Routing Peers - Quickstart for DNS servers on private networks
- DNS Settings - Disable DNS management for specific groups
- Troubleshooting - Fix common DNS issues
- API Reference - Automate with the API
Need help? Check our troubleshooting guide or join the NetBird Slack community.

